Running a command-line scan
Certain actions, such as running custom controls, can only be initiated through the command line.
Note: We recommend adding kubescape to your environment variables.
Basic commands
The simplest command is kubescape scan, which scans the cluster against all frameworks.
We recommend adding the --account option to send the scan information to ARMO Platform.
kubescape scan --account=XXXXXXXXX
We recommend these options to start with
kubescape scan --verbose --enable-host-scan --account--verbose: display all resources, including those that do not trigger a security control--enable-host-scan: turn on host scanning--account: create an account and scan results to the ARMO Platform
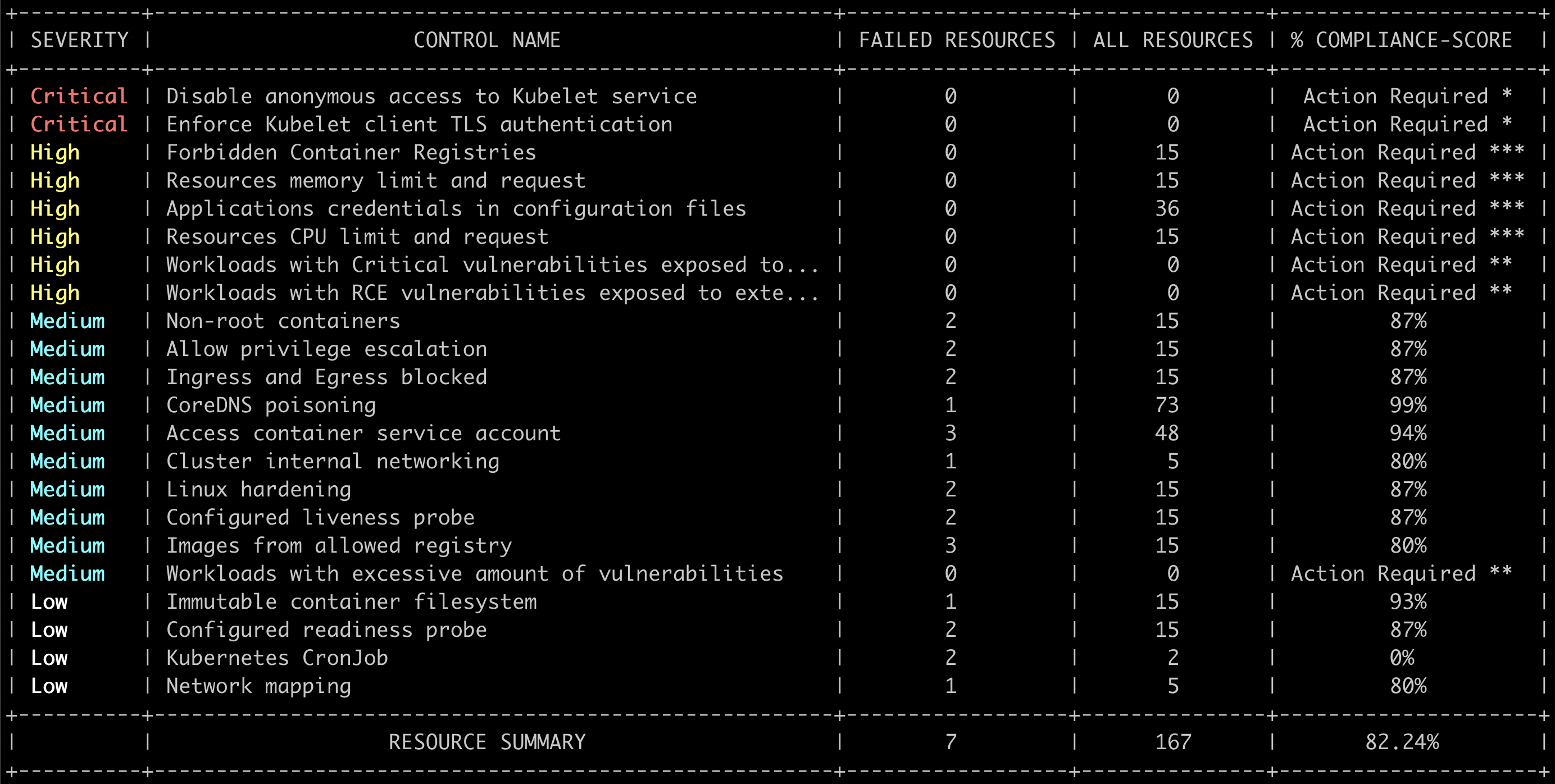
RBAC permissions
The following are the RBAC permissions required for Kubescape to scan a cluster.
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: kubescape-role
rules:
- apiGroups: ["*"]
resources: ["*"]
verbs: ["get", "list", "describe", "watch"]
# The host-scanner DaemonSet runs in a dedicated namespace applied by kubescape at the beginning of the scan. Kubescape will then remove the namespace once the scanning process is done
- apiGroups: ["apps"]
resources: ["daemonsets"]
verbs: ["*"]
- apiGroups: [""]
resources: ["namespaces"]
verbs: ["*"]
CLI-centric tasks
The following topics are CLI-centric, and describe how to perform actions using the CLI.
Updated 4 months ago
What’s Next
