Risk Spotlight
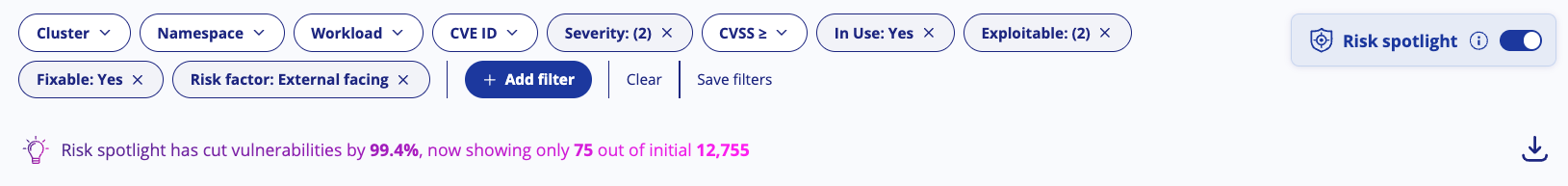
Risk spotlight prioritizes vulnerabilities that pose a real risk to your organization using workload configuration, runtime context, exploitability, severity, and fixability. It cuts the noise of your CVE scanning results by more than 90% and helps you focus on the alerts that actually matter.
For any organization, there could be a large number of vulnerabilities, considering the number of workloads and images. To make fixing them more manageable, Risk Spotlight adds a new way of prioritizing vulnerabilities based on runtime behavior. This can significantly reduce the number of vulnerabilities that need immediate attention, making the vulnerability management process more effective.
It does this by combining the following information:
- Entities that are external-facing
- Entities that have vulnerabilities such as:
This way, it leads users to focus on the workloads at most risk and cuts through the noise of CVE scan results, reducing them by over 90%. Thus, helping you focus on the alerts that actually matter.
Updated 3 months ago
