Nexus
Overview
ARMO platform allows you to scan container images from your Nexus Container Registry for vulnerabilities. This guide provides step-by-step instructions to connect your Nexus registry with the ARMO platform.
Prerequisites
- Access to the Nexus Repository Manager.
- An active ARMO account.
- Username and password with read permissions for the desired repository.
Quick Guide: Generating Nexus Registry Credentials
- Log in to the Nexus Repository Manager.
- Navigate to Security > Users in the Administration section of the Nexus dashboard.
- Create or identify a user account with the following permissions:
nx-repository-view-*-*-read(read-only access to all repositories).
- Copy the username and password for authentication.
Step-by-Step Guide
Step 1: Navigate to the Integrations Page
- Log in to the ARMO platform.
- Go to Settings > Integrations.
- Under Container Registries, click Connect for Nexus.

Step 2: Add a New Registry
-
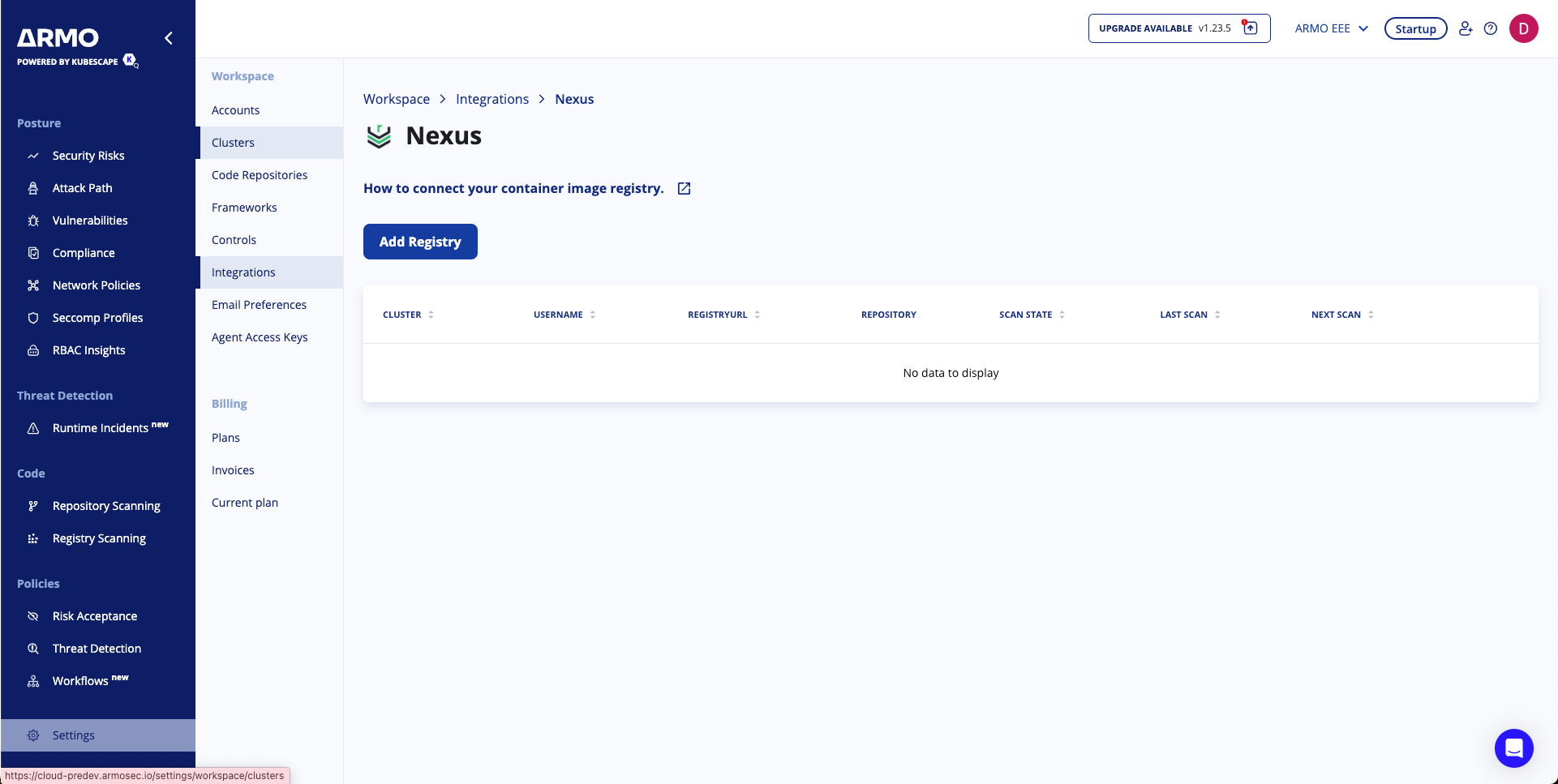
Click Add Registry to open the configuration panel.
-
Fill in the required details:
- Cluster: Select the cluster from which scanning will be initiated.
- Registry URL: Enter your Nexus registry URL (e.g.,
nexus.example.com). - Username: Enter the Nexus user account with read access.
- Password: Provide the password for the user account.
-
Click Next to continue.
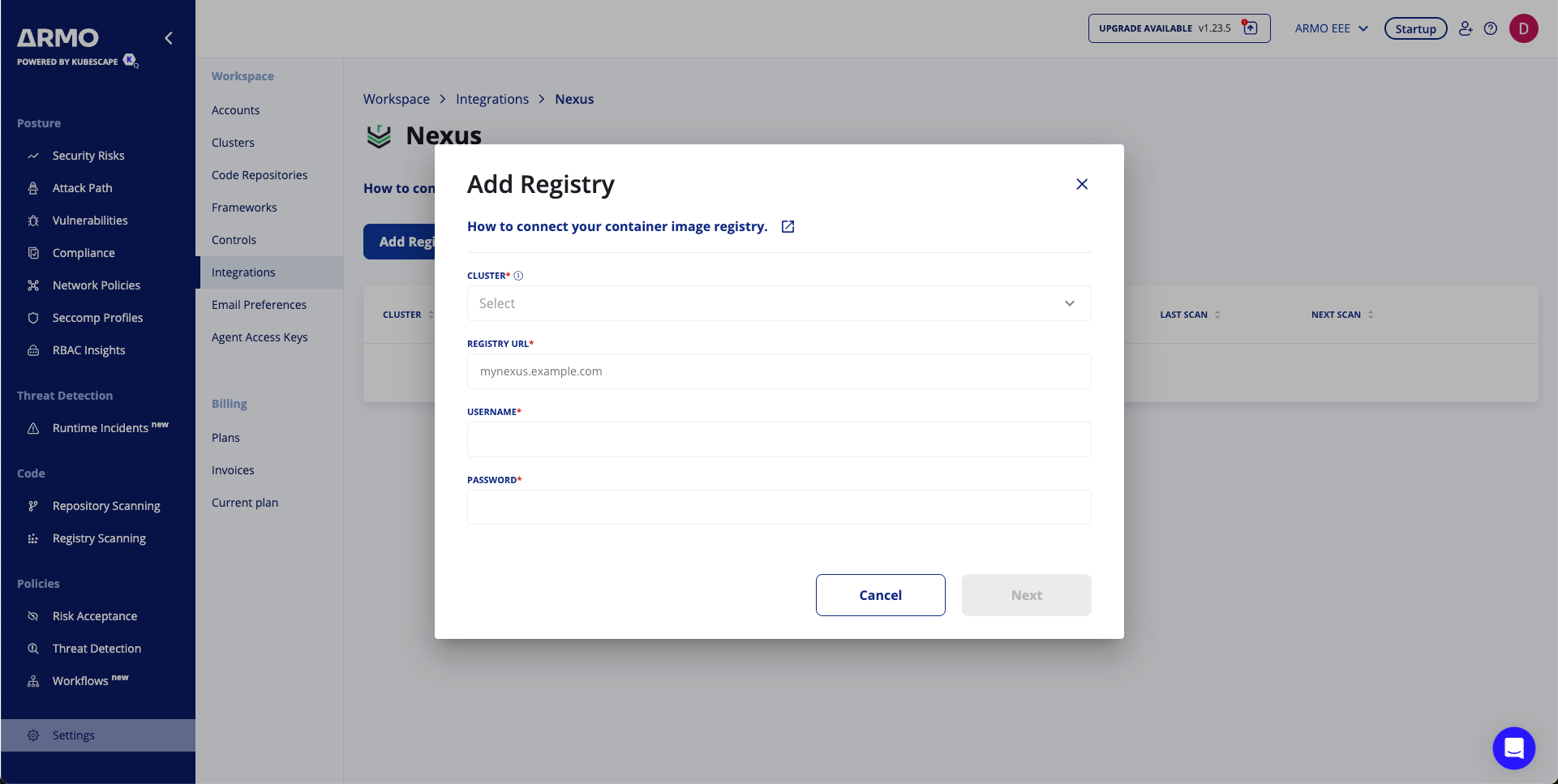
Step 3: Schedule Scans (Optional)
-
Select the repository to scan.
-
Configure periodic scans:
- Frequency: Set to daily or weekly.
- Time: Define the time in UTC.
-
Click Save to finalize the schedule.
Step 4: Finalize the Connection
- Review the details of your configuration.
- Click Save to activate the integration.
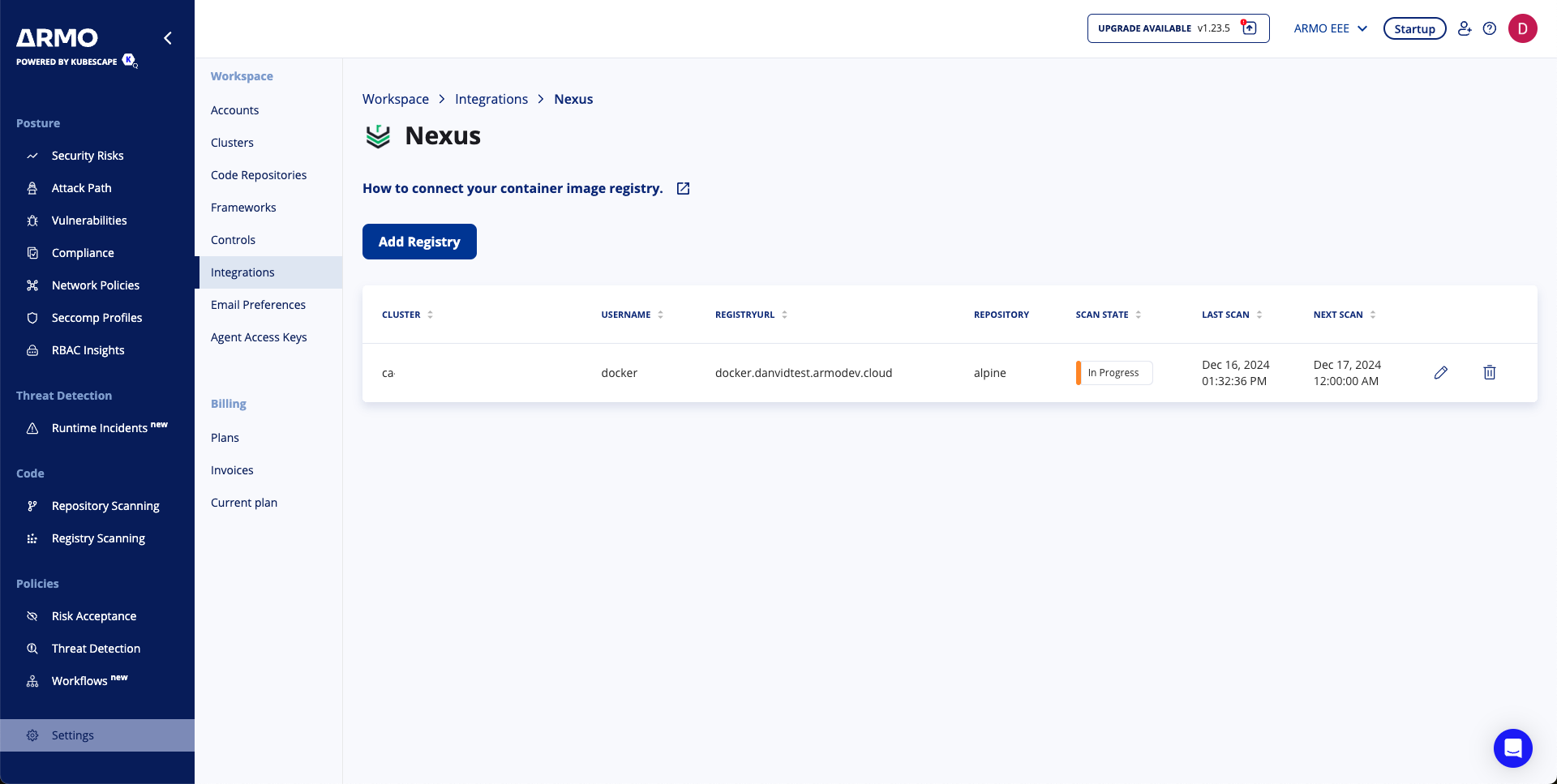
Your Nexus Container Registry is now successfully connected to the ARMO platform.
Conclusion
By integrating your Nexus Container Registry with the ARMO platform, you gain continuous visibility into the security of your container images. This integration enables automated scanning, timely detection of vulnerabilities, and actionable insights to maintain compliance.
Updated 3 months ago
