Vulnerabilities
Overview
This document outlines the process for appropriately handling vulnerabilities deemed acceptable temporarily, permanently, or until a fix is available. It ensures transparency and accountability while maintaining a robust security posture.
It helps ensure that vulnerabilities are properly assessed, and decisions to ignore them are made based on a thorough understanding of associated risks.
Best practice
The best practice is to fix or patch vulnerabilities or to remove the vulnerable dependency. However, if a reported vulnerability doesn't have a fix or you decide not to fix it, you can accept it. When you accept the vulnerability, ARMO platform does not consider it a violation.
Risk Acceptance for a Vulnerability
-
In the vulnerabilities tab for the selected workload, click the 3 dots menu for one of the CVEs --> Accept Risk
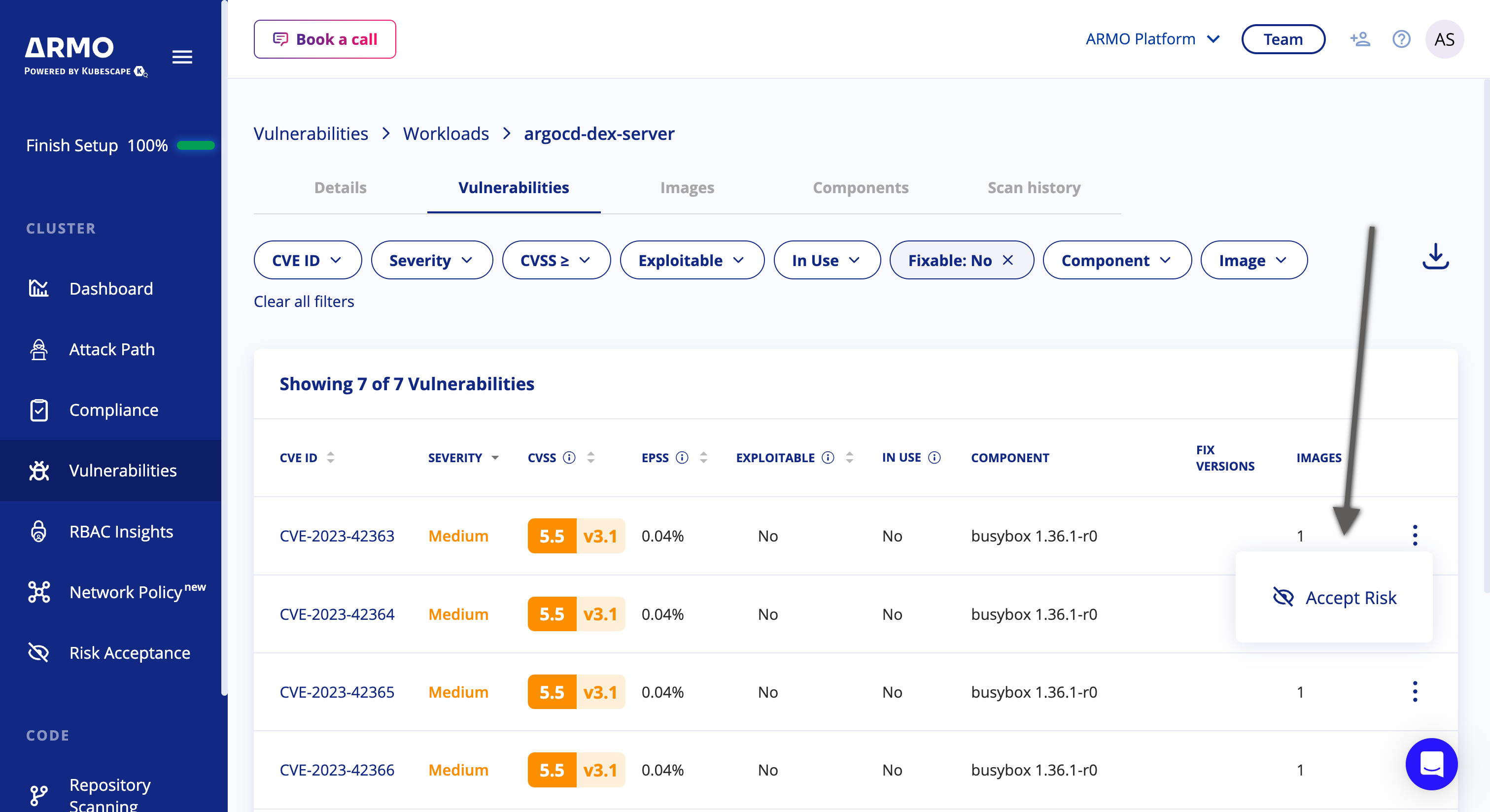
-
In the Accepting the Risk dialog, type the reason you want to ignore that CVE, and click Save.
If the CVE isn't fixable, you can accept it until there is a fix available.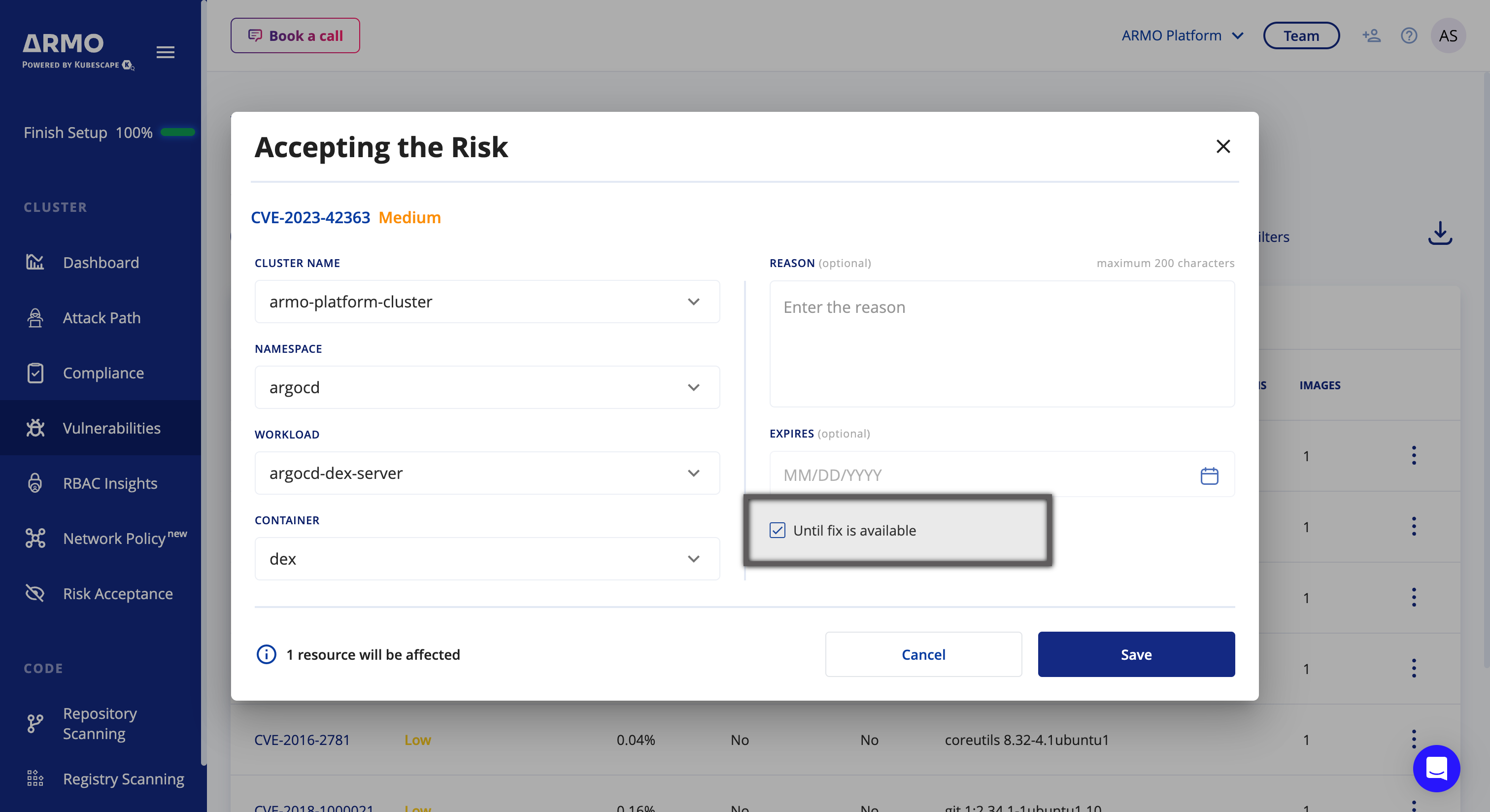
-
You should see a confirmation message at the top of the screen, indicating the CVE was accepted successfully, and on the next scan that accepted CVE will move to the Risk Acceptance page
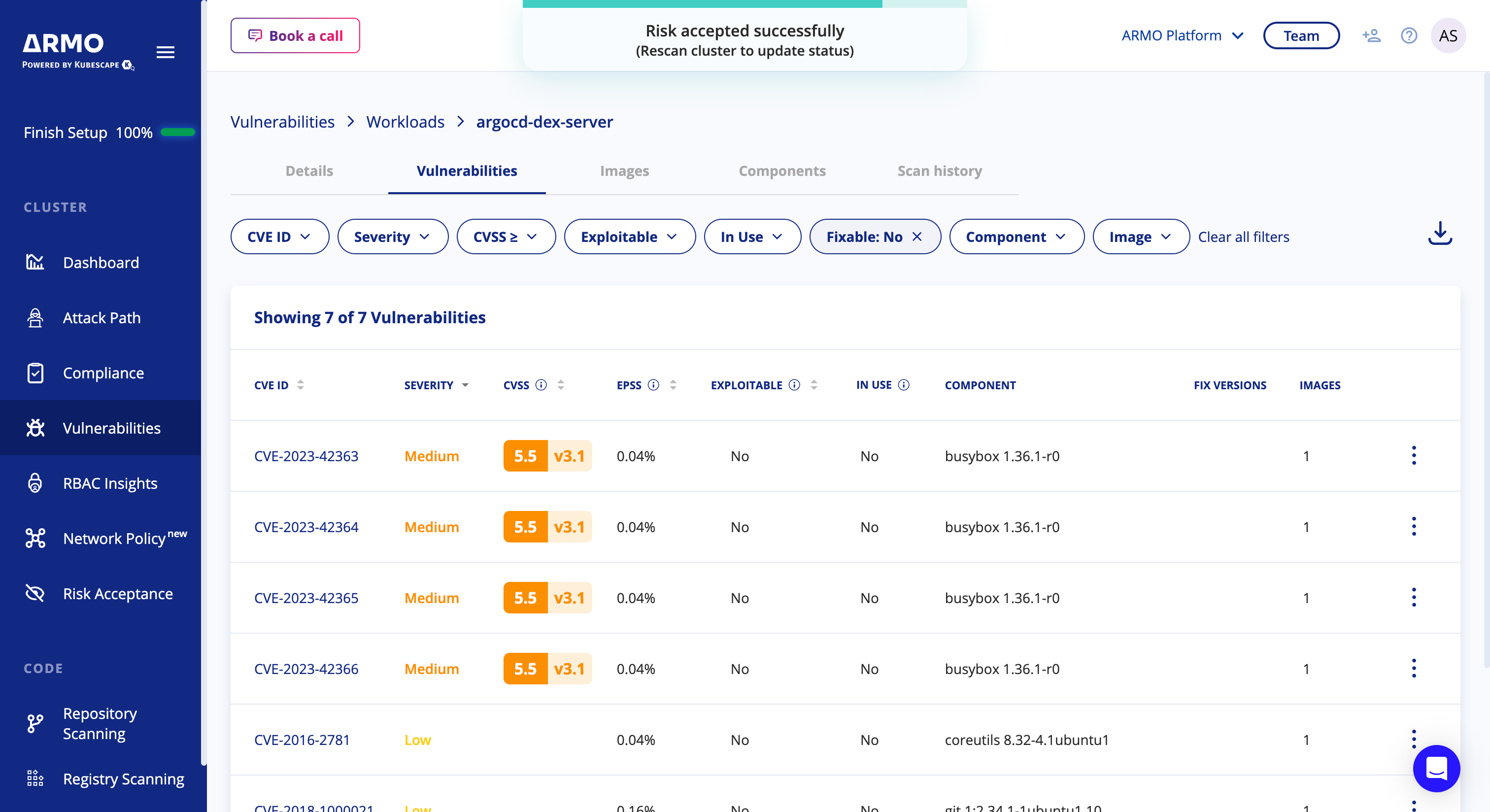
Future scans will not count accepted CVEs, and as a result, the number of vulnerabilities will decrease
Revoke an accepted risk
-
Open the Risk Acceptance page and click on the like for a CVE that was previously accepted
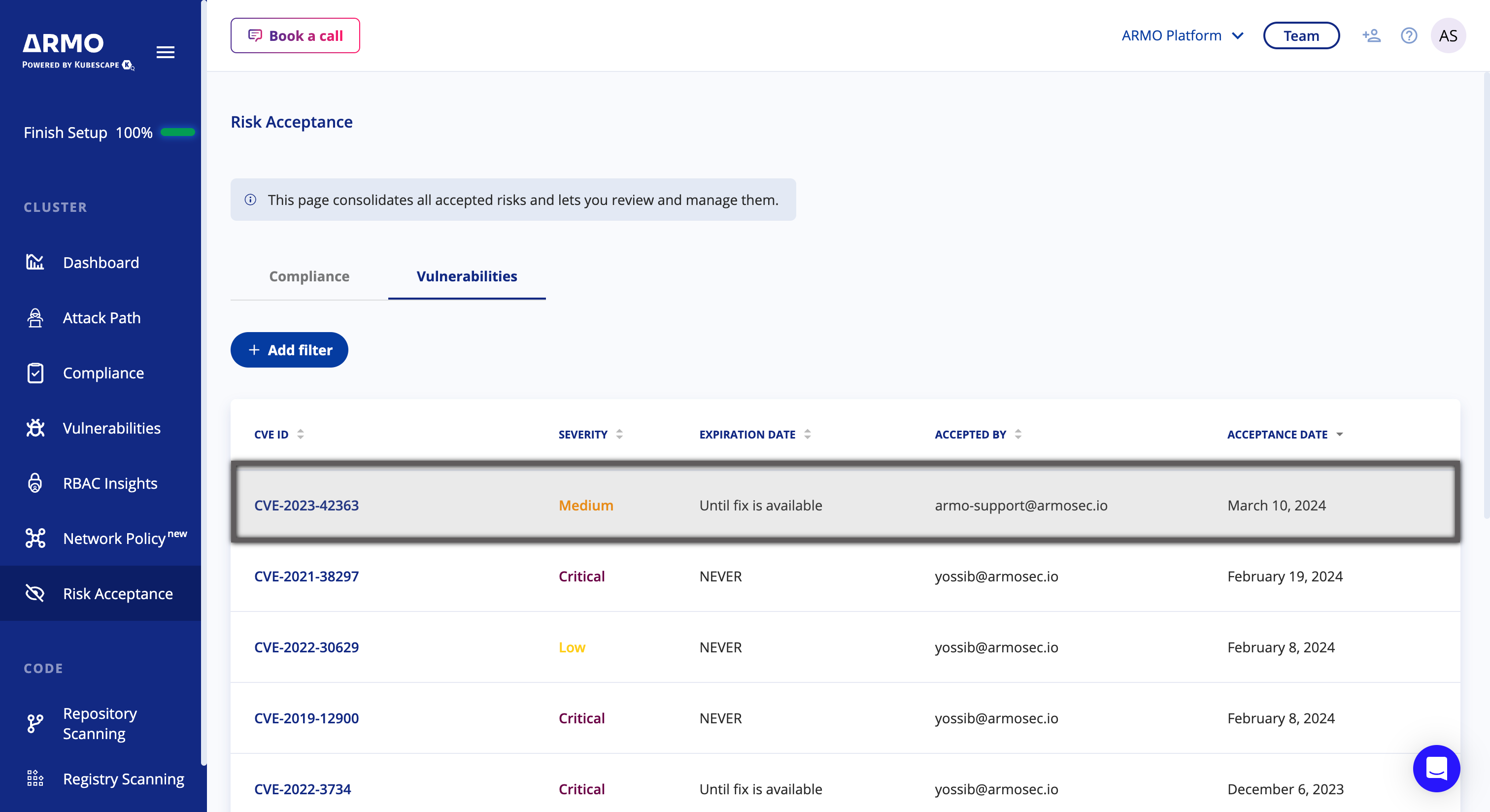
-
Click on the trash button
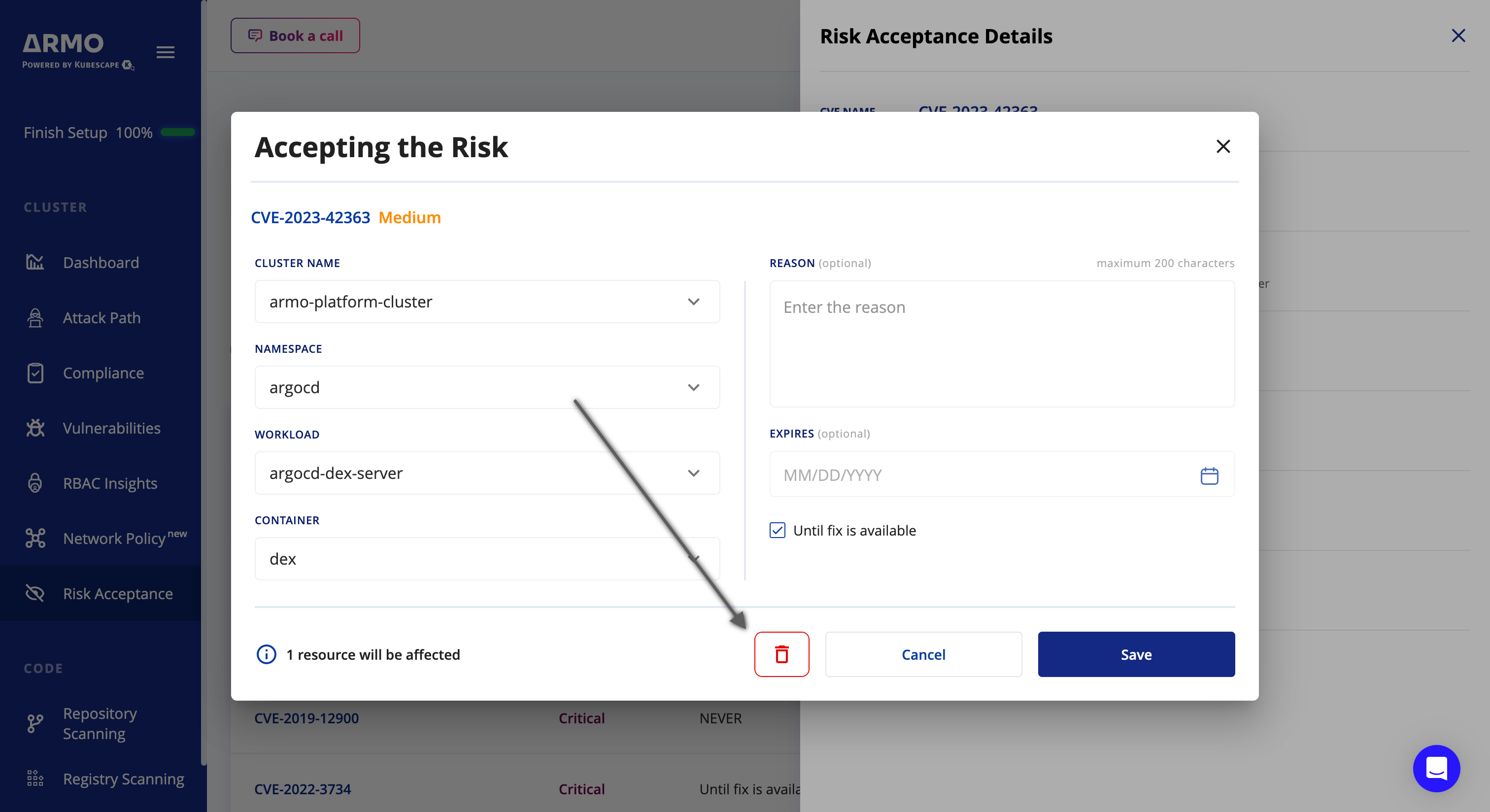
-
Confirm the revoke of the accepted risk
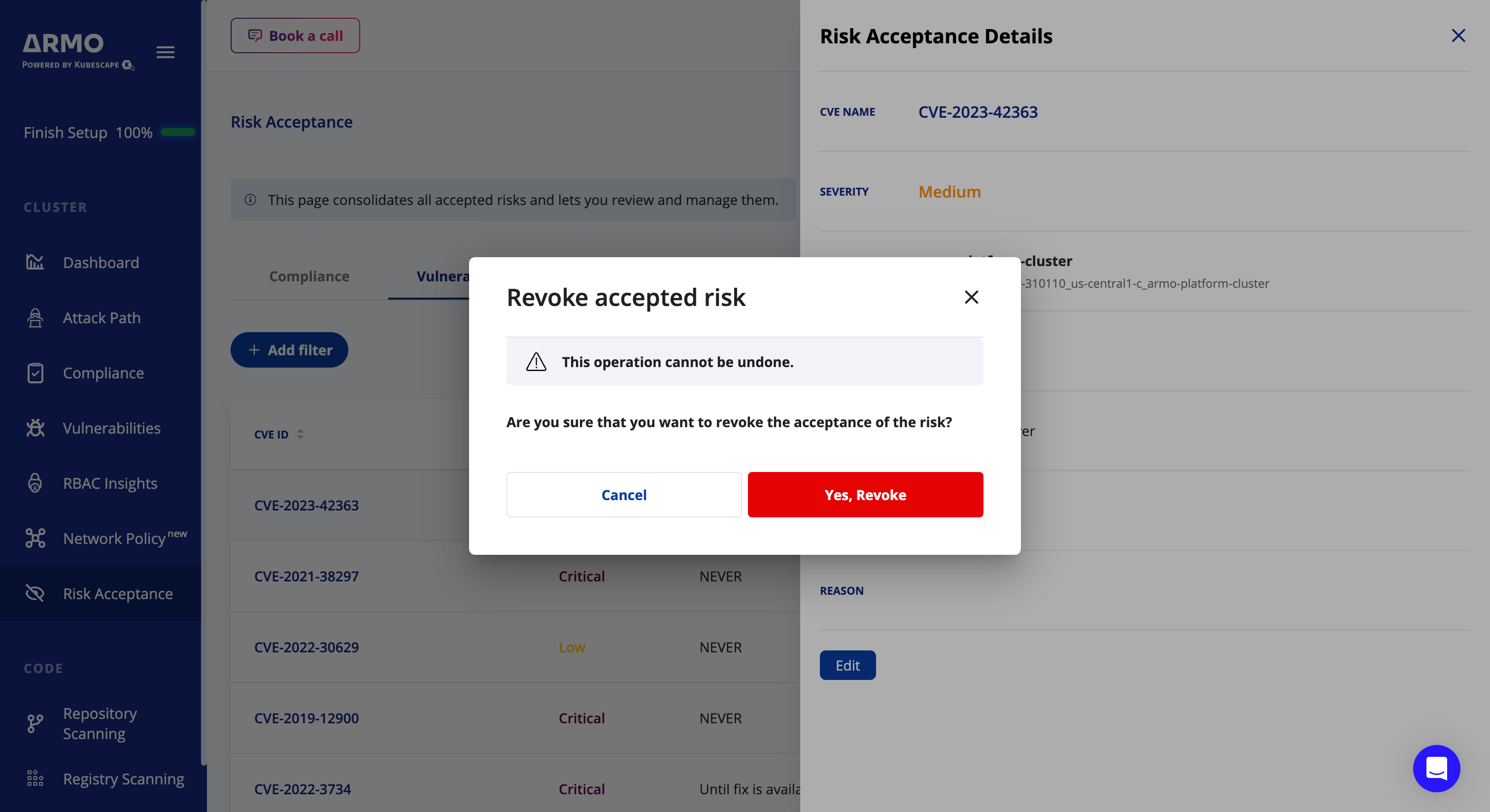
-
You should see a confirmation message at the top of the screen, indicating the accepted risk was revoked successfully
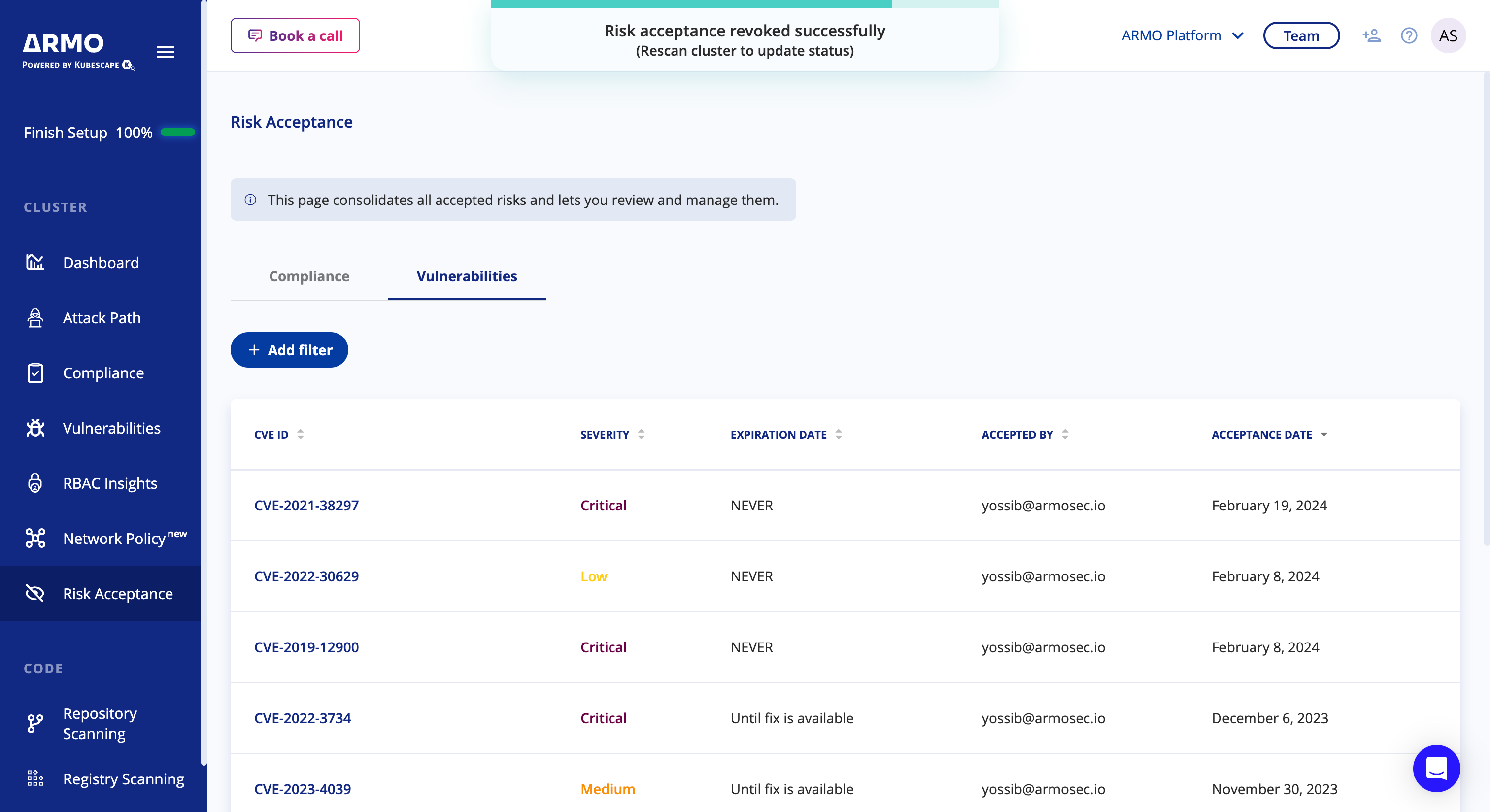
Updated 4 months ago
