Workloads View
ARMO Platform automatically analyzes and scans the container image of your workloads. It gives you a list of vulnerable workloads, and a Risk Spotlight, so you can concentrate on addressing the current, critical, and exploitable vulnerabilities.
Workload Scan Results Overview
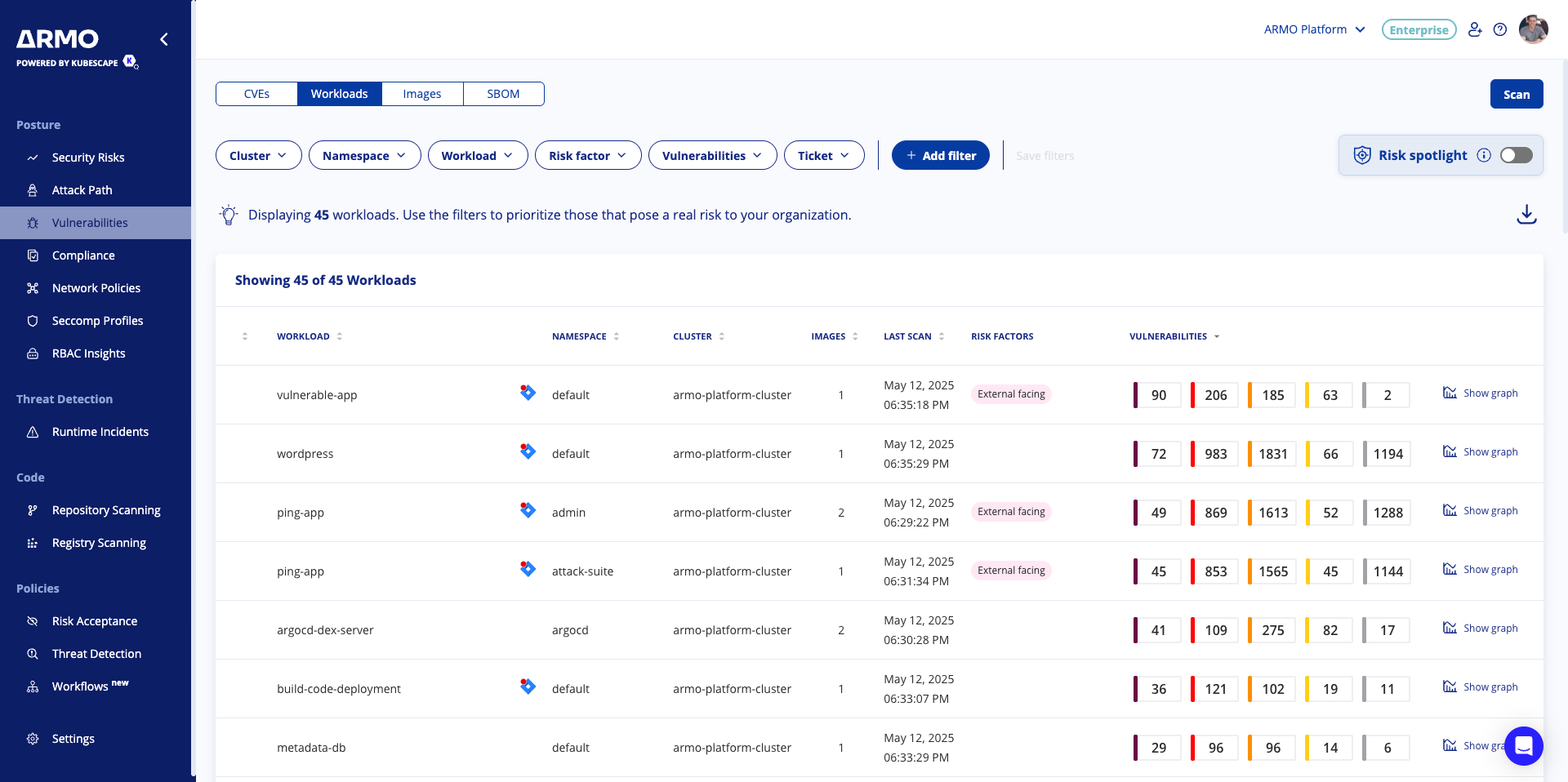
The workloads page lists the workloads scanned by ARMO Platform, ordered by the most vulnerable.
It allows users to filter results according to Risk factor such as:
- Internet facing - This workload is publicly reachable and exposed to external network traffic
- External facing - reachable from external networks, such as the internet or other networks outside the Kubernetes cluster.
- Privileged - has all the capabilities of the host machine, and is not subject to the limitations regular containers have. Practically, this means that privileged containers can perform almost every action that can be performed directly on the host.
- Secret access - can access and use sensitive information stored as secrets.
- Data access - identifies workloads that have mounted PVC. Workloads with PVC access can potentially expose sensitive information and elevate the risk of unauthorized access to critical resources.
- Host access - identifies all pods using hostPID or hostIPC privileges. The hostPID and hostIPC fields in a deployment yaml may allow cross-container influence and may expose the host itself to potentially malicious or destructive actions.
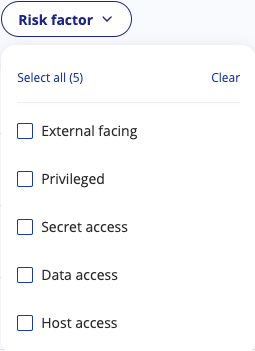
Additionally, turning data into information, the Smart vulnerabilities filter helps users focus on workloads that have vulnerabilities that fall under the following criteria:
- In Use - The vulnerable package is loaded into the memory
- Exploitable - The vulnerability can be effectively used by an attacker to compromise the integrity, confidentiality, or availability of a system or its data. (Based on EPSS and CISA-KEV)
- Fixable - The vulnerability can be remediated by applying a patch
- Severity - Indicated by the Common Vulnerability Scoring System (CVSS), assesses the potential impact of a security vulnerability on a scale, helping prioritize and address the level of threat it poses.
Workload details
Provides an overview of all the workload details such as cluster, namespace, risk factors, labels, and vulnerabilities by severity.
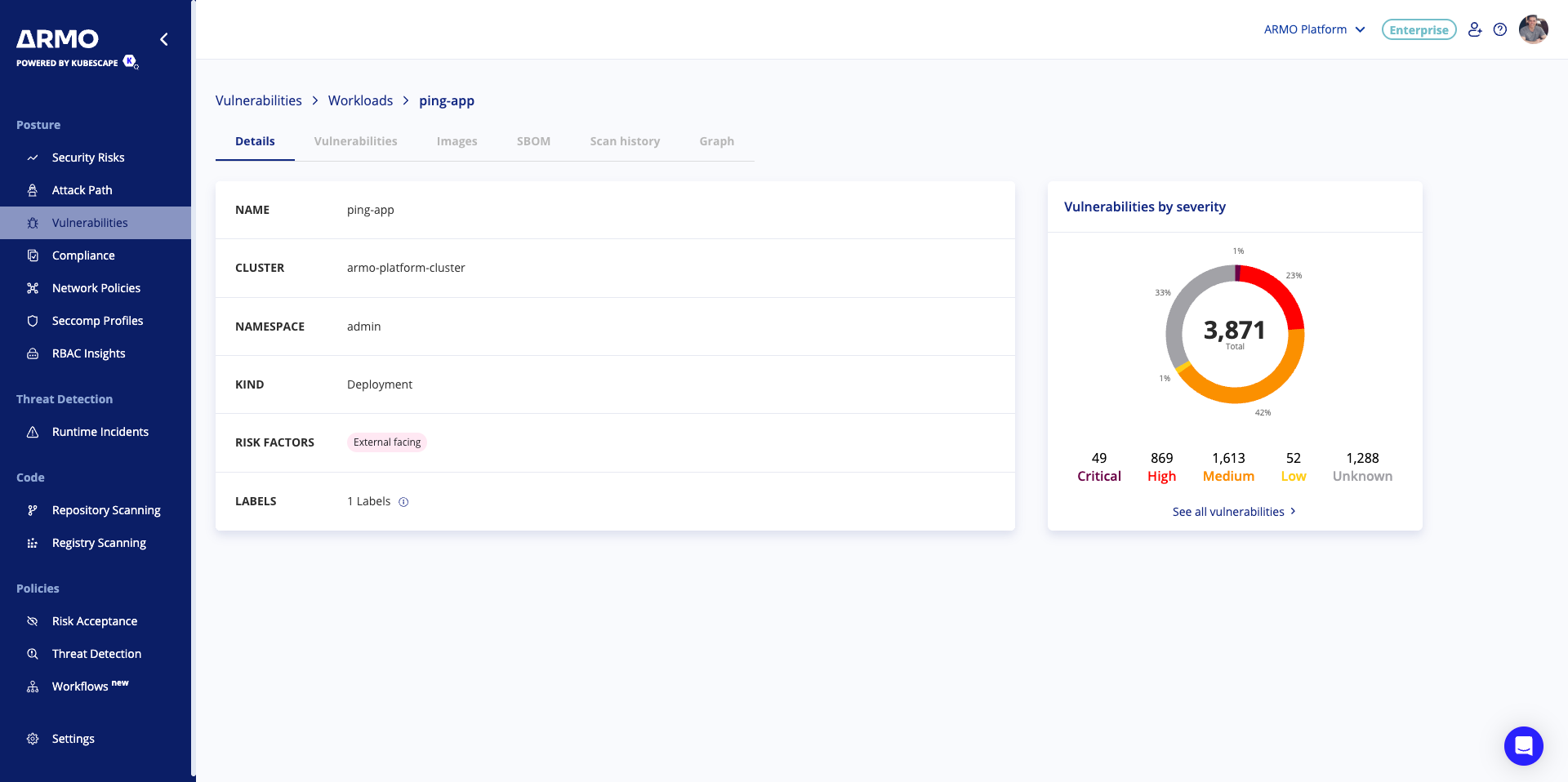
Understanding the workload risk
Once the risk spotlight toggle is on, click on the vulnerability tile to better understand the workload risk and how to mitigate it.
The Vulnerability details page shows the risk spotlight filters and explains how to fix the exploitable vulnerabilities
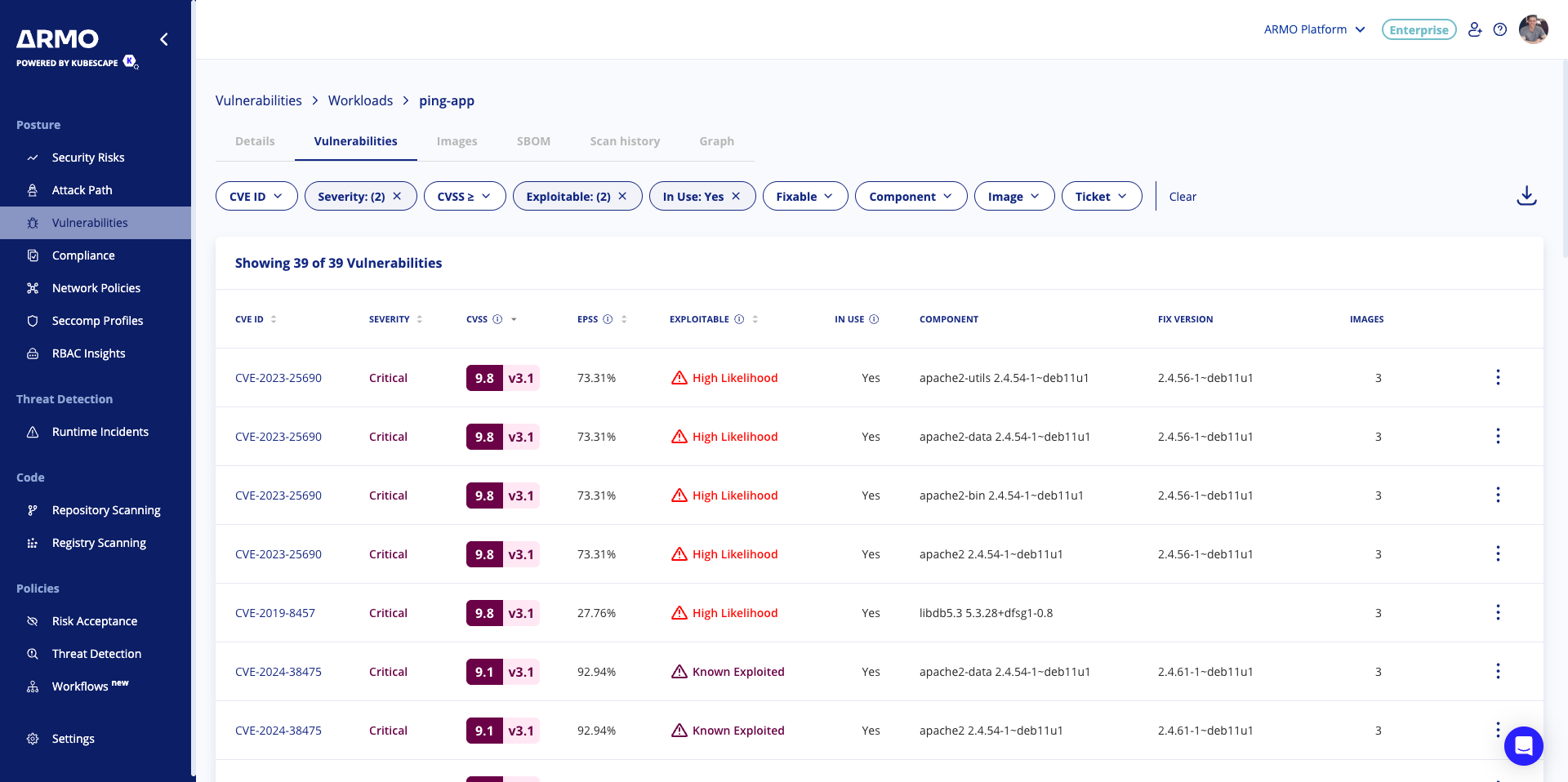
CVE details
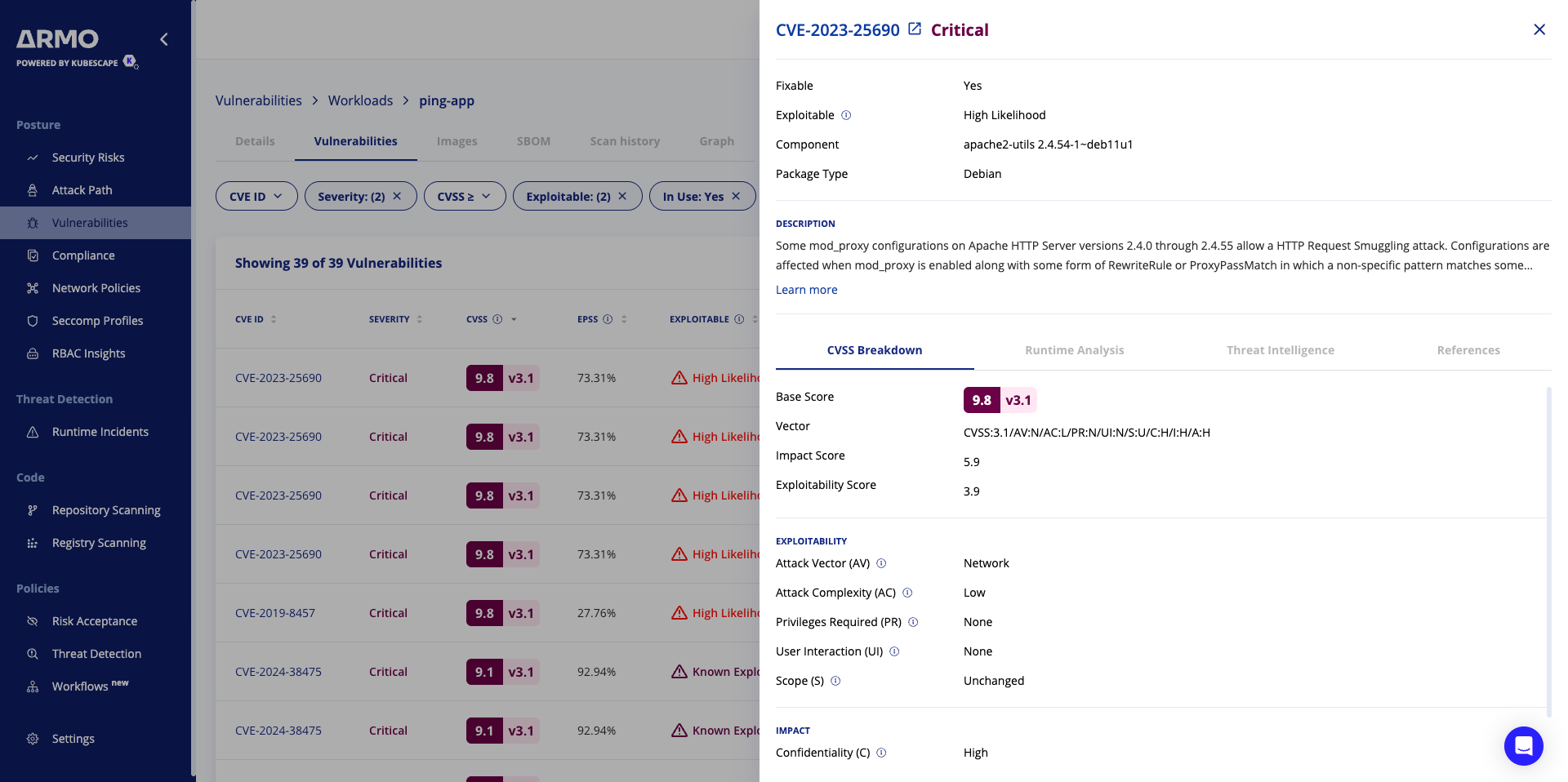
Threat Intelligence
EPSS
We have introduced EPSS(Exploit Prediction Scoring System) as a new security input for prioritizing vulnerabilities. EPSS attempts to quantify the probability of a particular vulnerability (CVE) being exploited using various inputs such as code execution, CVE age, or known exploits.
CISA KEV
If a CVE is listed in the CISA (Cybersecurity & Infrastructure Security Agency) KEV (Known Exploited Vulnerabilities) catalog, it means that the CVE has been confirmed to be actively exploited by threat actors. This catalog serves as a resource for organizations and security professionals to prioritize the mitigation of vulnerabilities that pose an immediate risk to their systems and networks. Therefore, vulnerabilities listed in the CISA KEV catalog should be addressed with urgency to prevent potential security breaches or compromises.
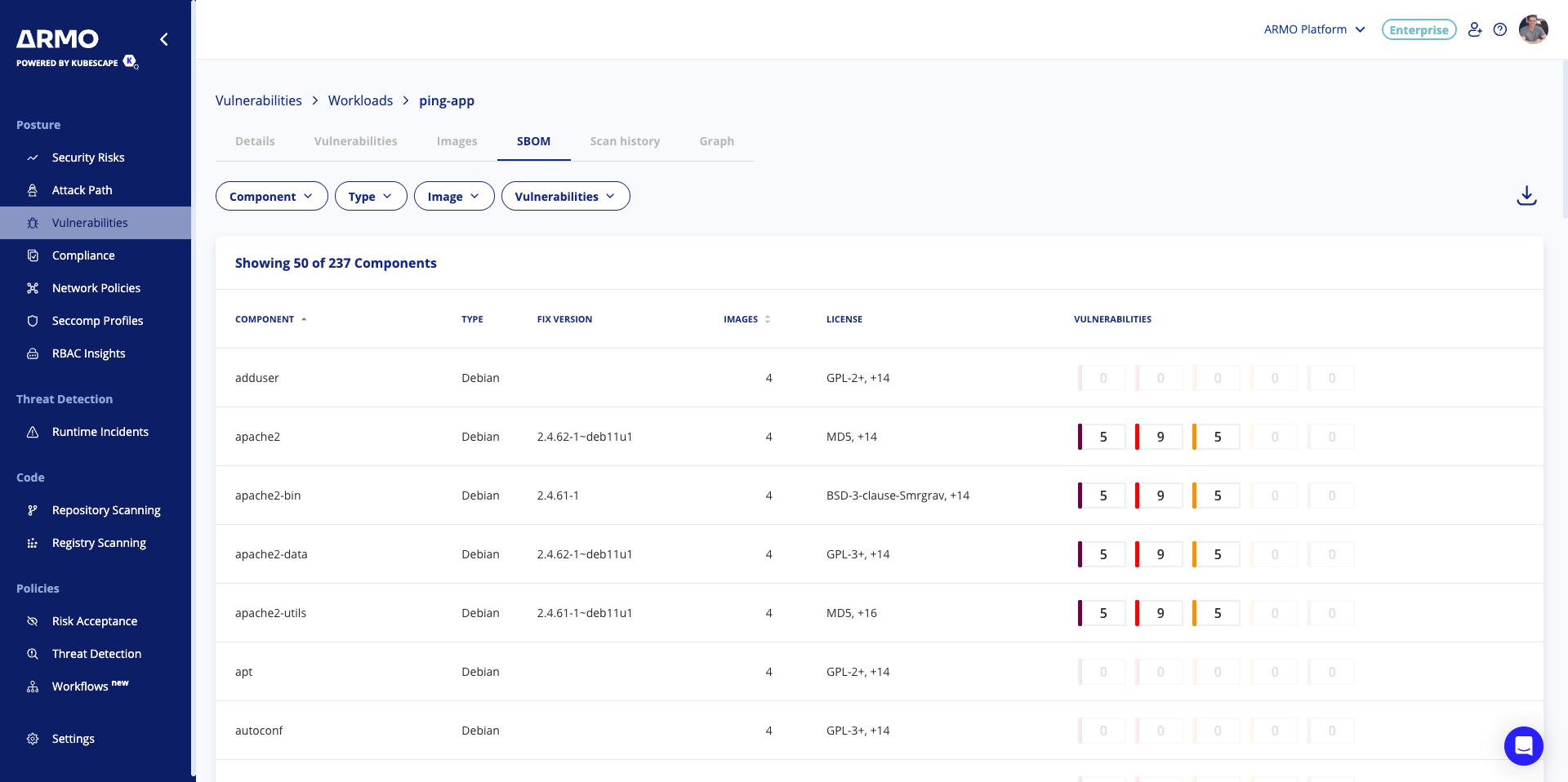
Workload SBOMs
During vulnerability scanning, ARMO Platform checks the active workloads and hosts. It then creates a runtime list of software components for each target called SBOM (Software Bill of Materials). This SBOM is sent to the workload components view for matching vulnerabilities.
Why generate SBOMs at runtime?
- Dynamic Environment Tracking: In rapidly changing environments, where workloads and their dependencies may change frequently, generating SBOMs at runtime allows for an up-to-date and accurate representation of the software components in use.
- Real-time Vulnerability Assessment: By having a runtime SBOM, security systems can perform real-time vulnerability assessments, identifying and addressing security issues as they emerge.
- Incident Response: In the event of a security incident, having a runtime SBOM aids in the rapid identification of affected components, helping security teams respond promptly and effectively.
- Compliance and Auditing: Generating SBOMs at runtime supports compliance efforts by providing a detailed and current inventory of software components, aiding in auditing processes, and ensuring adherence to security policies.
When examining the details of a workload, there is the possibility to view the components in it, effectively giving a view of the SBOM.
Exporting SBOM
Click on the Export button to download a CSV of your workload's vulnerable SBOM
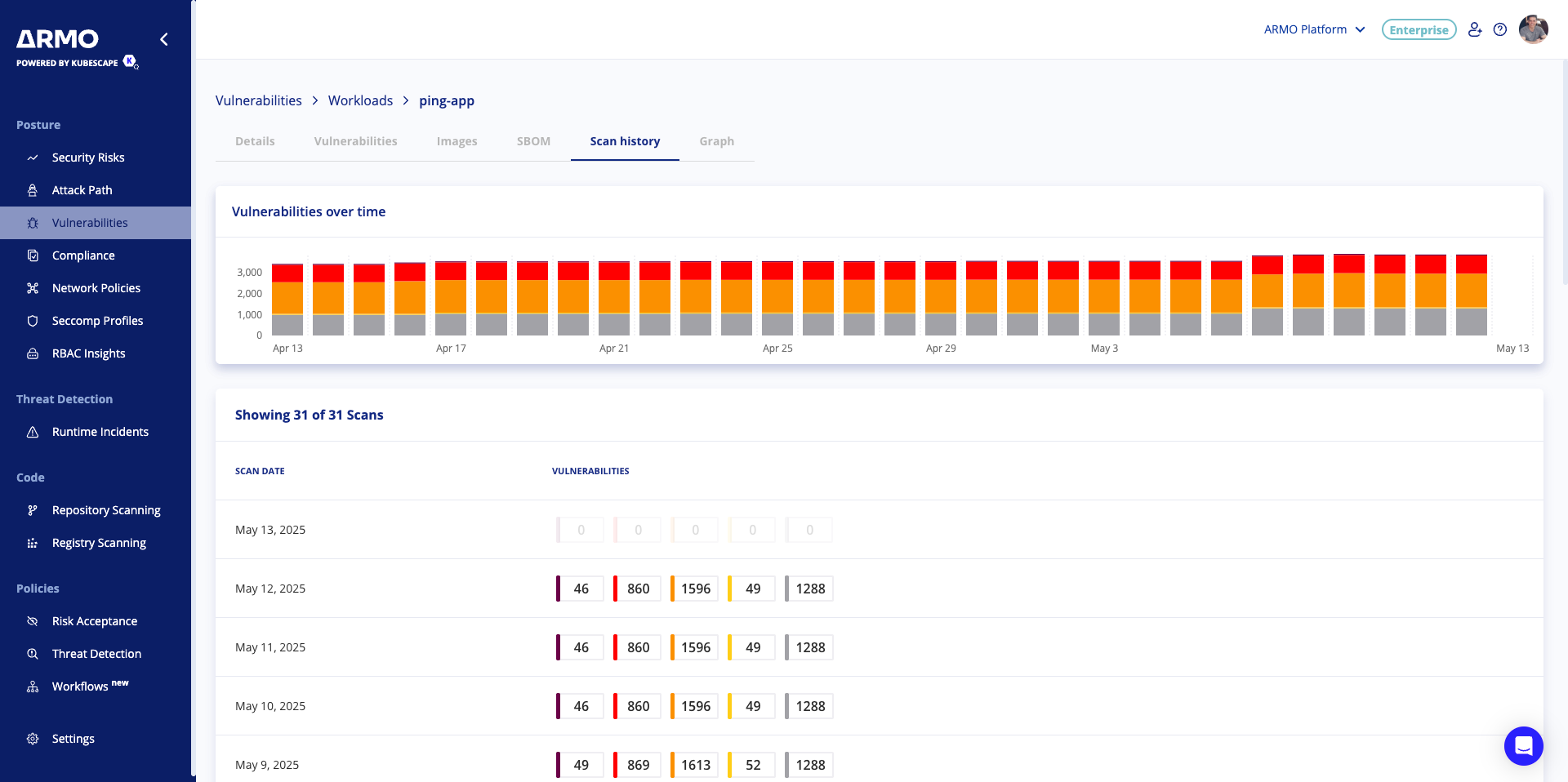
Scan history
Accepting a Risk
If your organization determines the CVE is an acceptable risk, you can accept the risk for that CVE by clicking on the 3 dots menu --> Accept Risk. See Risk acceptance for vulnerabilities for more information.
Updated about 2 months ago
