Attack Path
Introduction
An attack path is the sequence of steps an attacker takes to exploit security weaknesses, starting from an initial point of entry to the ultimate target, aiming to steal confidential data, demand ransom, or sell sensitive information. Along the way to valuable assets, attackers exploit vulnerabilities or misconfigurations in the environment to access specific resources and navigate from one to another.
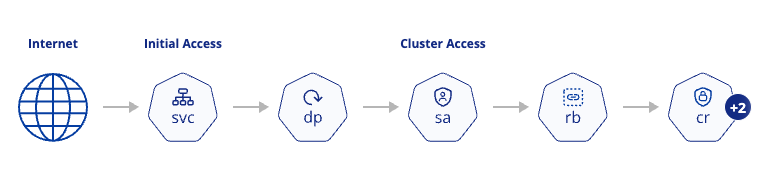
The attack path is displayed as a node-graph, with each node representing a step an attacker can execute. Each node provides details about its role within the attack and the exploitable weaknesses (misconfigurations or vulnerabilities) it has.
Overview: Explore Attack Paths
Go to the "Attack Path" page to view all the detected attack paths in your environment. By viewing all the ways attackers can exploit your environment, you’ll be able to understand your Kubernetes exposure level better and assess your general security status.
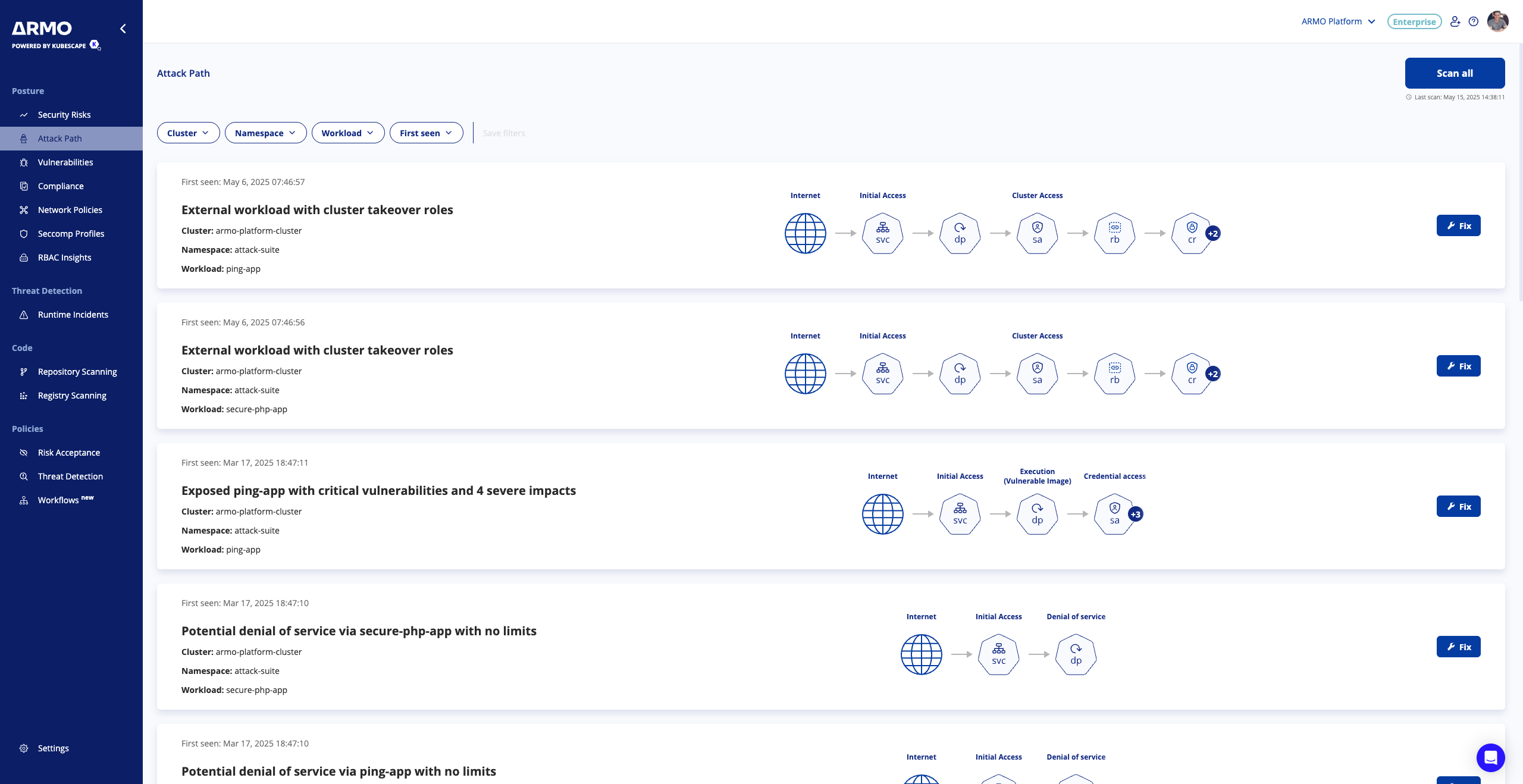
For each attack path, we’ll visualize it and provide the metadata (cluster, namespace, and workload). On top of that, you can:
- Filter the attack paths by cluster, workload, namespace, or the date of detection.
- Update the list of attack paths by clicking "Scan all," which triggers scans across connected clusters to identify if new attack paths were detected or existing ones were resolved.
- To get more information about a specific attack path click, click either the “Fix” button or directly on the card.
Fixing an attack path
Once you've decided to fix a specific attack path, simply click the 'Fix' button to see more details about the attack.
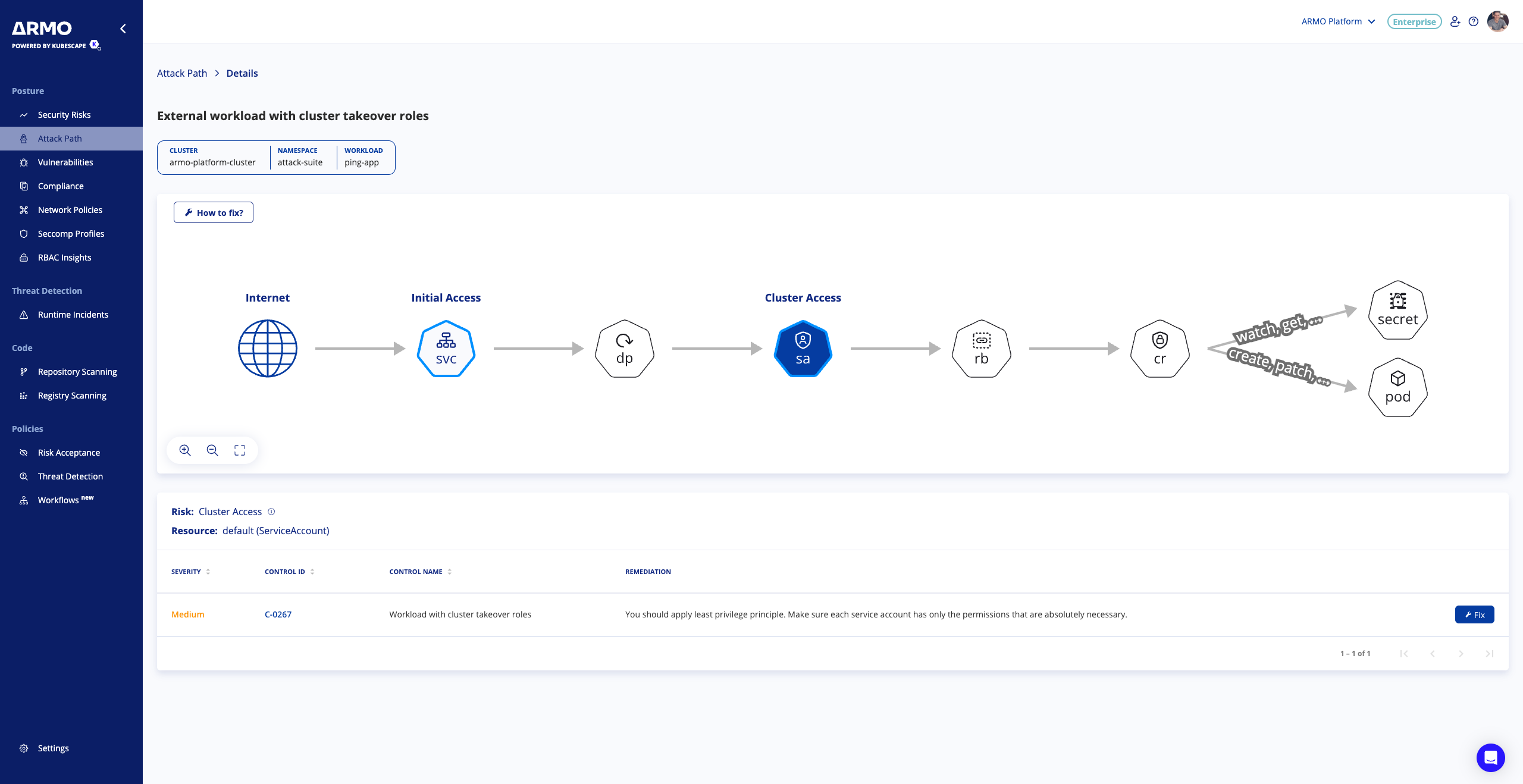
On the left side, you'll find a visual representation of the attack path, while the right side displays a table outlining the misconfigurations or vulnerabilities of the picked node.
Attack path graph
The attack path is visualized as a node graph, where each node represents a potential step in the attack and its associated vulnerabilities or misconfigurations. Nodes marked with a "+" sign indicate multiple types of resource kinds for that particular step. Simply hover over a node to view the resources involved in that step, and click on it to uncover its specific misconfigurations or vulnerabilities.
Attack path steps
| Step | Risk |
|---|---|
| Initial Access | An attacker can access the Kubernetes environment. |
| Execution (Vulnerable Image) | An attacker can execute malicious code by exploiting vulnerable images. |
| Data Collection | An attacker can gather data. |
| Secret Access | An attacker can steal secrets. |
| Credential Access | An attacker can steal account names and passwords. |
| Lateral Movement (Network) | An attacker can move through the network. |
| Persistence | An attacker can create a foothold. |
| Privilege Escalation (Node) | An attacker can gain permissions and access node resources. |
| Denial of service | An attacker can overload the workload, making it unavailable. |
Misconfigurations/Vulnerabilities table
The table shows the vulnerabilities or misconfigurations that were detected on the picked node. To get more information about how to remediate them, click on “Fix” or “Details”.
How to fix the attack path?
To block an attack path, focus on “securing a node.” This means resolving the security issues associated with a single node—these issues could be misconfigurations or vulnerabilities
Updated 4 months ago
