Authentication
Connecting ARMO Platform with SSO
ARMO enables third-party authentication SSO using SAML or OIDC to its Platform. This enables you to associate your account with all e-mails coming from an authorized domain name.
Please set up the required SAML or OpenID Connect application with your identity provider.
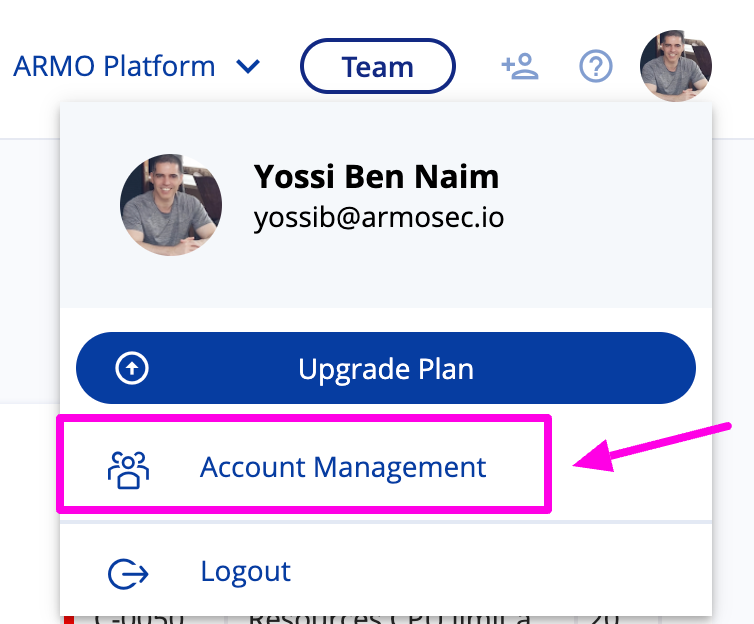
Then go to the ARMO Platform and open the Account Management as follows:
Click on the SSO menu on the left navigation, and then click Setup SSO Connection
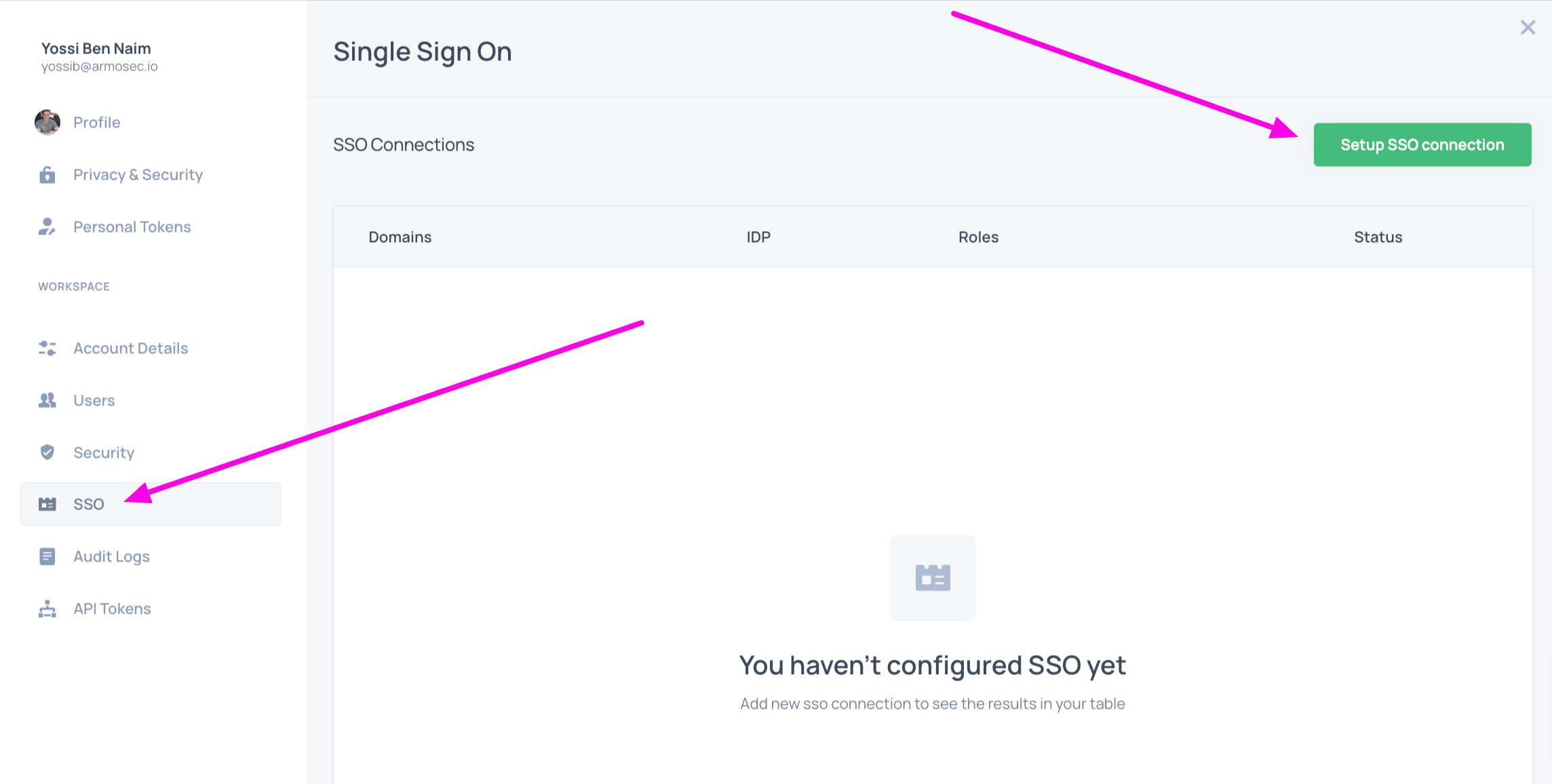
Select your IDP in the following dialog

References
Updated 3 months ago
