Hosts View
Overview
The ARMO Platform enables you to detect and monitor vulnerabilities across your cloud infrastructure, both in agentless and agent-based modes.
This capability provides continuous visibility into host security risks in your AWS cloud environment and on your Kubernetes nodes, helping you strengthen your infrastructure posture without manual effort.
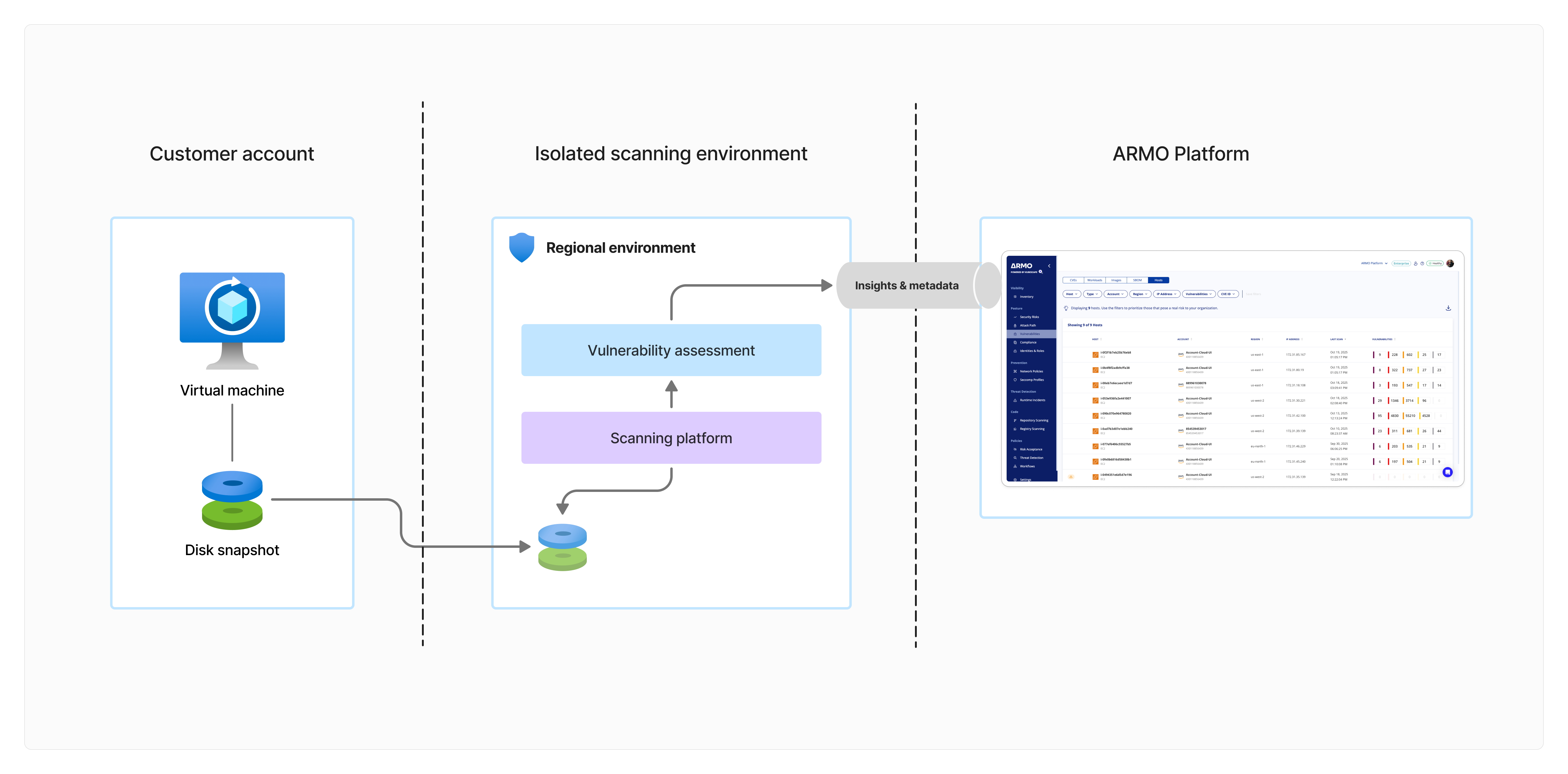
Agentless Host Scanning
Agentless Scanning allows ARMO to identify and report host-level vulnerabilities across your AWS cloud environment without requiring the ARMO Agent to be installed.
This provides a quick, low-touch way to assess vulnerabilities across your infrastructure while maintaining strong data privacy controls.
You can deploy Agentless Host Scanning by onboarding your cloud accounts through the Cloud Account Onboarding Wizard.
Note:
You can apply tags to limit instance, or disk access scope on your infrastructure. Tags can be defined before connecting the account (recommended) or later.
How It Works
Once Agentless Host Scanning is enabled for your connected AWS environment:
- Automated Scheduling:
ARMO automatically schedules vulnerability scans at 24-hour intervals. - Snapshot Creation:
The Agentless scanner gathers metadata and dependencies of each VM instance, then creates a temporary snapshot. - Scanning Process:
The snapshot is analyzed to extract a list of installed packages and versions. - Data Transmission:
The package list is securely transmitted to ARMO for vulnerability analysis. - Snapshot Deletion:
After scanning, snapshots are automatically deleted, ensuring no persistent data remains.
This entire process is designed to be non-intrusive, automated, and privacy-preserving.
Data Privacy & Security
ARMO’s Agentless scanner only sends a list of installed packages required for vulnerability analysis.
No sensitive data ever leaves your infrastructure.
ARMO does not transmit:
- System or package configurations
- Encryption keys or certificates
- Logs or audit trails
- Business-sensitive or personal data
This ensures compliance with organizational and regulatory security standards.
Exclude/Include Resources from Vulnerability Scanning
When you connect your AWS environment to ARMO Vulnerability Host Scanning, all Elastic Compute Cloud (EC2) instances with root volumes are included in the scan by default.
You can customize the scope of scanning using AWS tags to exclude or include specific resources.
Excluding EC2 Instances
To exclude certain EC2 instances from being scanned, assign exclusion tags to them in the AWS Console or through AWS APIs on the instance scope
We recommend setting these tags before initiating the first scan.
If you add exclusion tags after onboarding, the change will take effect in the next scheduled scan.
Including Data Volumes in Scans
By default, ARMO scans only the root volumes of EC2 instances.
To also include additional volumes in the scan, apply inclusion tags as described below.
Tagging Semantics
You can apply the following tags at the volume or EC2 level.
Tags can be added or modified at any time to adjust scan inclusion or exclusion.
| Scope | Key | Default | Description |
|---|---|---|---|
| Instance | armo:secure:vulnscan:scan | true | Controls whether the EC2 instance is included in vulnerability scans. |
| Volume | armo:secure:vulnscan:scan | false | Determines whether the volume (non-root) is included in scans. |
Enable Agentless Host Vulnerabilities Scanning
- Follow the onboarding wizard to connect your AWS environment.
- On the connection Wizard ensure to select CSPM > EC2 vulnerability
- Once the connection is established, ARMO will automatically start the first agentless scan within 15 minutes.
- Scan results appear in Vulnerabilities > Hosts
Scan Frequency: Every 24 hoursFirst Results: Within ~60 minutes of enabling the connection
By default ARMO is scanning Stopped and Running EC2 instances
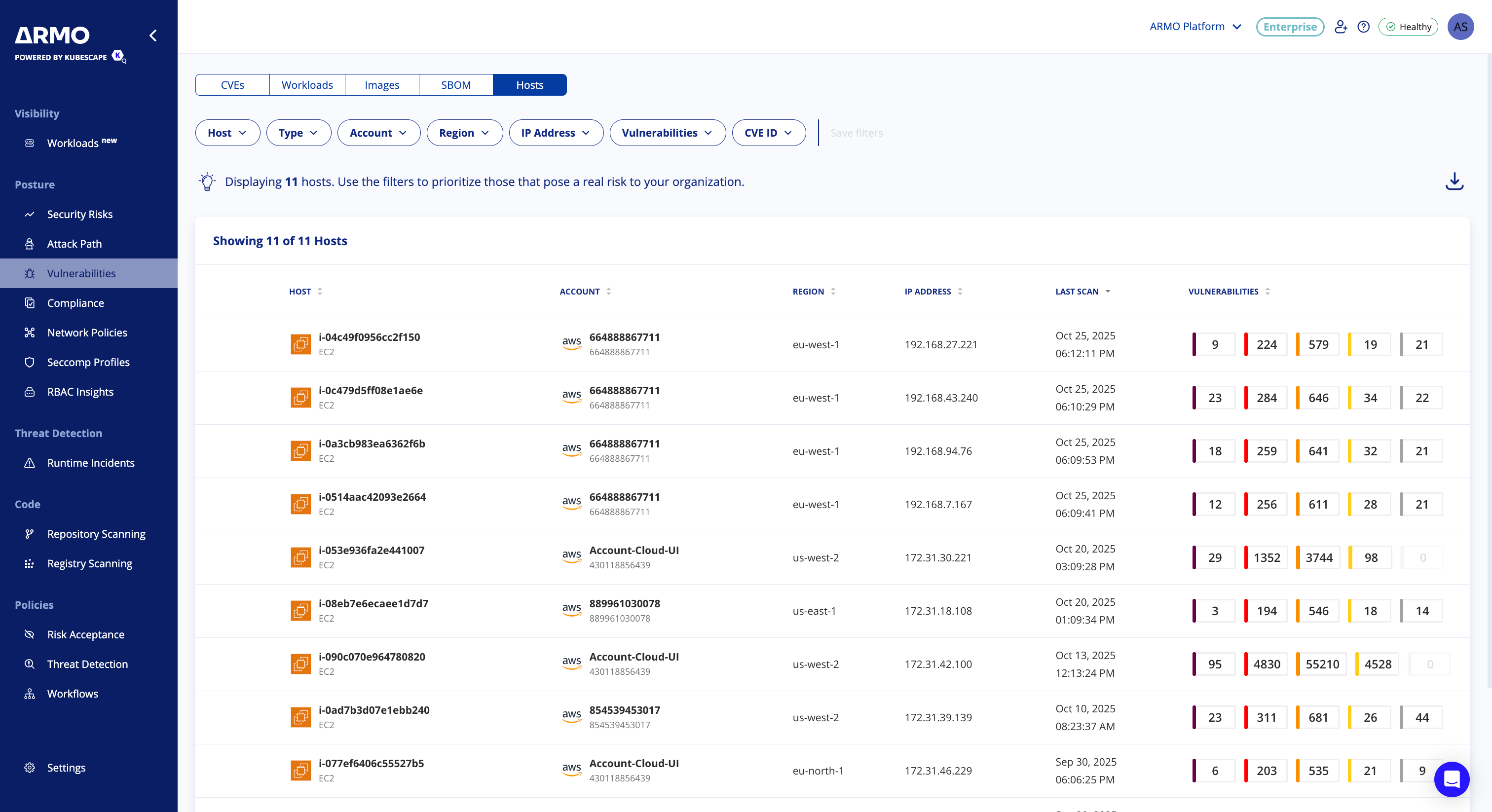
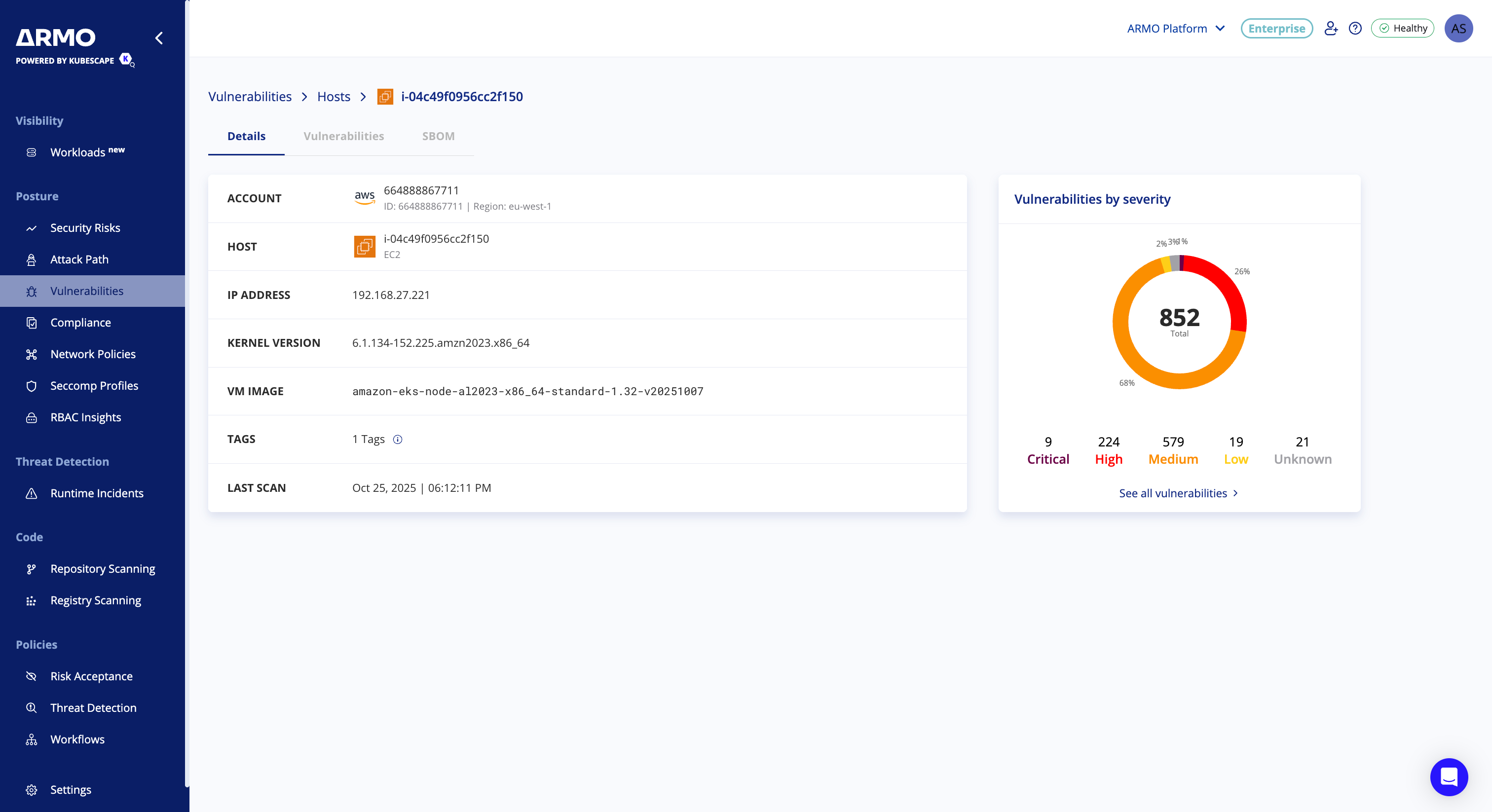
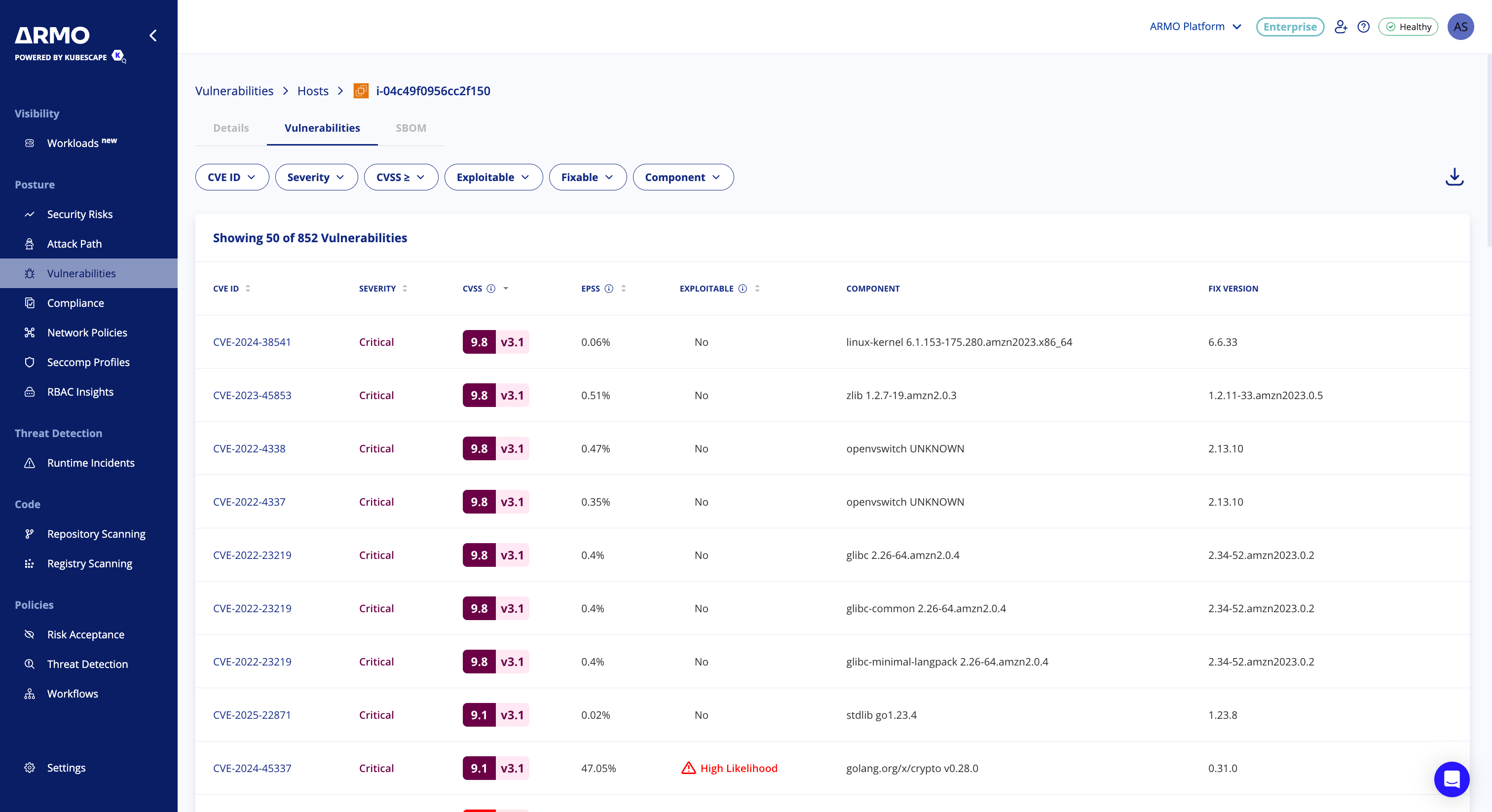
View Host Vulnerabilities Scan Results
You can view discovered vulnerabilities for your AWS EC2 hosts under Vulnerabilities > Hosts
Each finding includes:
- Hostname, instance ID and private IP address
- Cloud account and region
- Severity (Critical, High, Medium, Low)
- CVE details and remediation guidance
Continuous Scanning
ARMO automatically performs continuous scanning through a scheduled job that runs every hour.
Each run performs the following actions:
- Discover new instances: If new instances are detected, they are automatically scanned.
- Remove inactive instances: Instances that no longer exist in the customer account are removed from the scan inventory.
- Re-scan existing instances: If an instance’s last scan (start time) occurred more than 24 hours ago, it is scanned again.
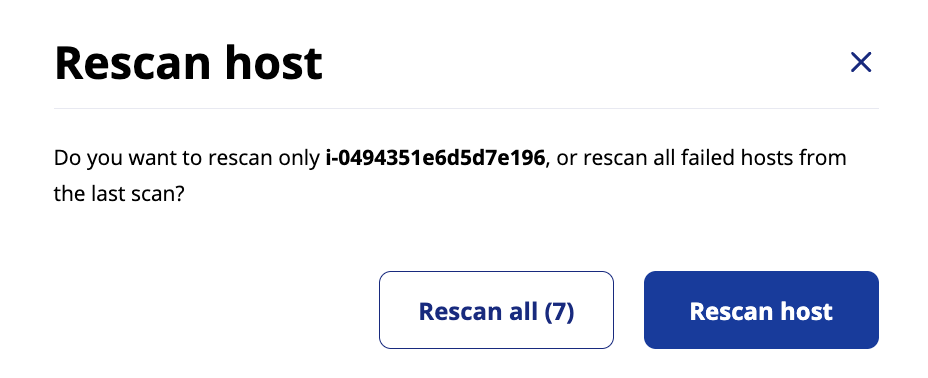
Force Rescan of Failed Scans
ARMO allows you to rescan instances that previously failed during a scan. Users can select one or more failed instances in the ARMO interface and trigger a rescan manually. This flexibility ensures that all instances are properly scanned, even if prior attempts failed.
Agent-Based Host Scanning (Coming soon)
Agent-Based Host Scanning uses the ARMO Agent to continuously assess vulnerabilities directly on the host, providing deeper visibility into runtime conditions and configurations.
This method complements Agentless Scanning by offering in-depth insights into workloads running on Kubernetes clusters, VMs, or bare-metal hosts.
Usage and Integration
Once scanning (agent-based or agentless) is active, ARMO automatically correlates host vulnerabilities with runtime workload findings, providing a unified security view.
All host findings are managed under the Vulnerability > Hosts, which can be customized to trigger alerts, suppress false positives, or export data for further analysis.
Feature Limitations
The following features are currently not supported for agentless host scanning:
- Risk Spotlight
- Risk Acceptance
Future releases will extend these capabilities.
Scanning Limitations
Storage limit – when the combined size of all volumes attached to an instance is greater than 1200 GB, or an instance has more than 8 volumes attached to it, ARMO will skip the scanning of that EC2 instance
Updated 3 months ago
