Scanning clusters
After installing our helm chart on your cluster you can scan your cluster for vulnerabilities and misconfigurations.
Add a cluster
You can add more clusters to your vulnerability and compliance scans. As more worker nodes are scanned, you might need to update your billing plan.
If you add a large cluster, you can adjust Kubescape’s resource usage. See Adjusting resource usage for your cluster.
- Navigate to Settings, and then click Clusters.
- Click Add Cluster, and then copy and paste the code in a terminal connected to the new cluster.
- Click Verify installation after Kubescape has been successfully installed on the cluster.
Manually trigger a scan
Clusters are automatically scanned twice a day–once for vulnerabilities and once for misconfigurations, but you can trigger a manual scan at any time.
Trigger a compliance scan
- Navigate to the Compliance page, and then click the cluster you want to scan.
- Click Scan, and then select a framework.
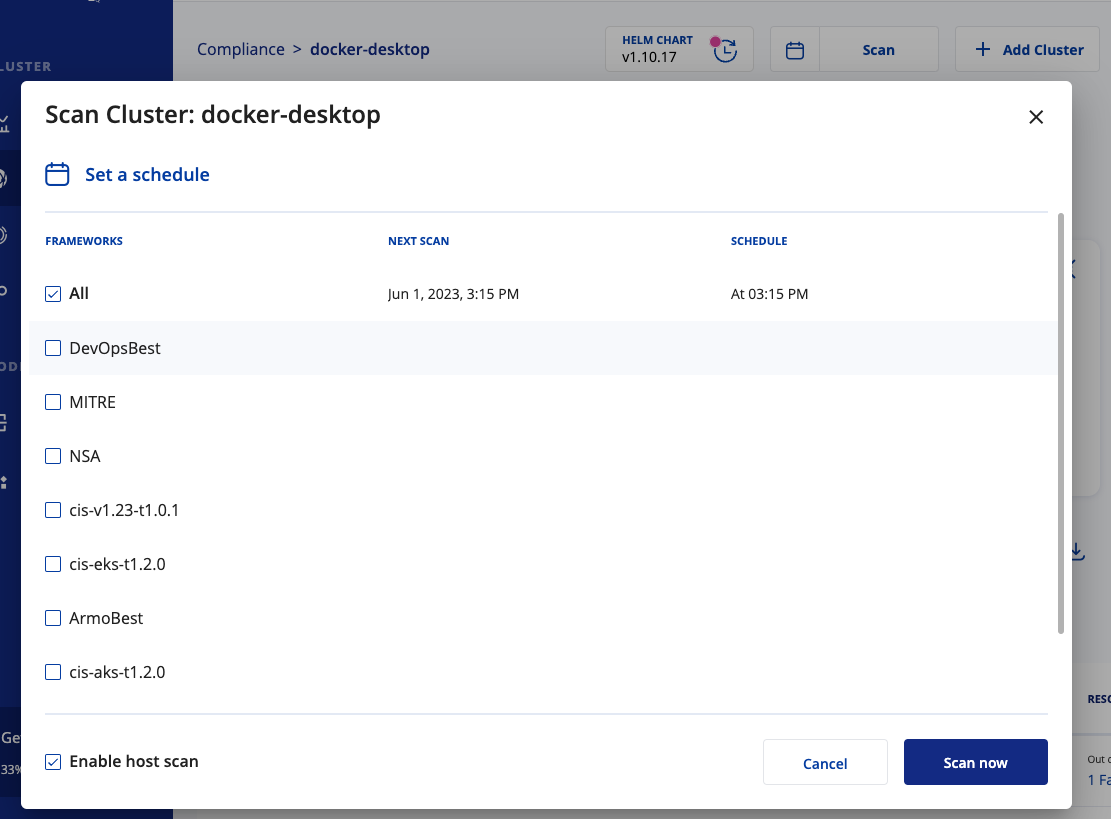
- If you want more information about nodes in your cluster, select Enable host scan. For more information, see Host scanning.
- Click Scan now.
Kubescape scans your cluster and sends the results back to ARMO Platform. The new scan is available within a few minutes.
Trigger a vulnerability scan
- Navigate to the Vulnerabilities page, and then click the cluster you want to scan.
- Click Scan, and then select a cluster.
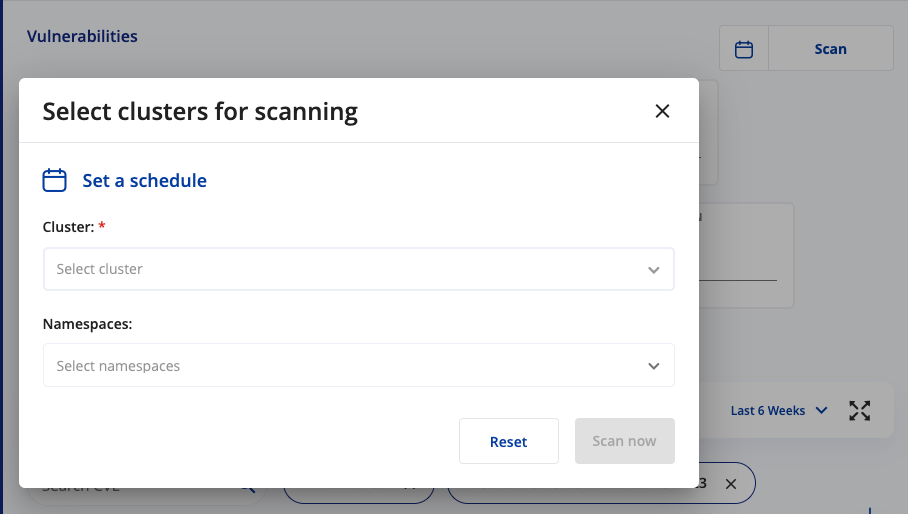
- If you want to limit the scan to a specific namespace, select the namespace from the list. By default, all namespaces are included.
- Click Scan now.
We scan your cluster for vulnerabilities and send the results to ARMO Platform. The new scan is available within a few minutes. For more information about the vulnerability scanner, visit the Kubevuln repository.
Schedule scans
You can schedule compliance and vulnerability scans to occur when you want. You must use Cron syntax to schedule the scans.
Schedule a compliance scan
- Navigate to the Compliance page, and then click the cluster you want to scan.
- Click the calendar.
- Enter when you’d like the scan to occur using Cron syntax, and then select a framework.
We do not recommend disabling host scanning. Host scanning is how we retrieve the information necessary to validate and run all the controls in the frameworks.
- Click Apply.
A CronJob is added to the cluster that initiates a scan at the set time. You can view or edit your scheduled scans in Settings > Clusters.
Click the three vertical dots, and then click Scheduled Scans.
Schedule a vulnerability scan
- Navigate to the Vulnerabilities page, and then click the cluster you want to scan.
- Click the calendar.
- Enter the when you’d like the scan to occur using Cron syntax, and then select a cluster.
- If you want to limit the scan to a specific namespace, select the namespace from the list. By default, all namespaces are included.
- Click Apply.
A CronJob is added to the cluster that initiates a scan at the set time. You can view or edit your scheduled scans in Settings > Images.
Click the three vertical dots, and then click Edit.
Updated 3 months ago
