Getting started
This guide starts when you are prompted to create an account and walks you through creating an account, scanning your cluster, interpreting the scan results, and provides next steps to explore.
Before you begin
You need access to a Kubernetes cluster that includes permissions to install. The cluster should also have Helm installed.
Create an account
- Navigate to cloud.armosec.io\ to create an account.

- Enter your email address and name, and then click Sign up.
After your account is created, you are prompted to connect to your Kubernetes cluster.
Scan a cluster
ARMO Platform provides a CLI command to deploy ARMO's helm chart. This command uses Helm(Note: Helm needs to be installed).
-
Copy and paste the command in the terminal connected to your cluster.
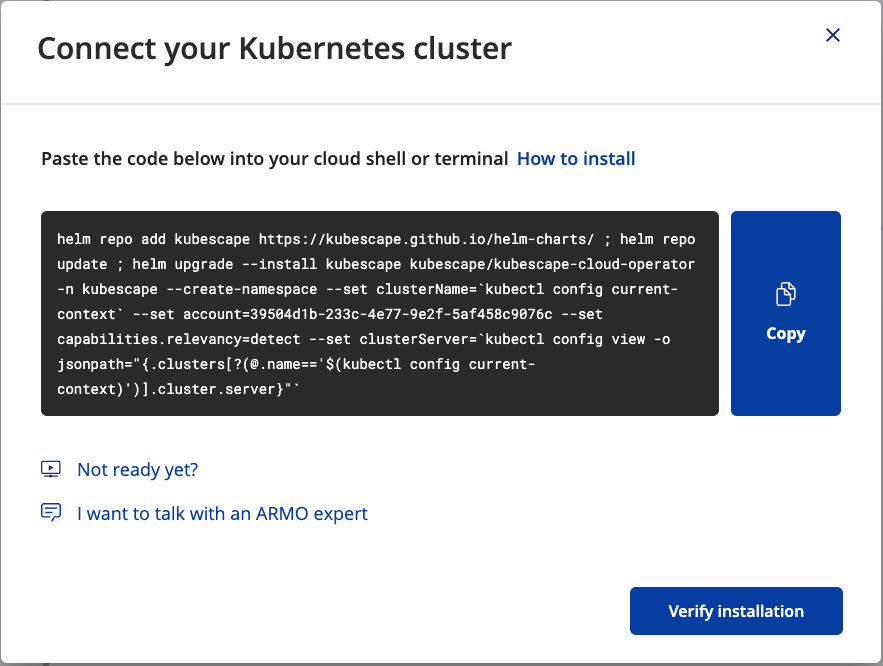
ARMO is downloaded and deployed.
-
Click Verify installation to test the connection between your cluster and ARMO Platform.
-
If the connection is successful, Kubescape scans your cluster against the default frameworks and submits the scan results to ARMO Platform. If you encounter any errors during deployment, consult the Installation Troubleshooting page.
Your cluster is scanned for misconfigurations and vulnerabilities, the results are sent to ARMO Platform.
Evaluate Results
After your first successful scan, the Security Risks automatically opens with your cluster’s scan results. The Security Risks is the section in ARMO Platform where you can get a high-level overview of your Kubernetes environment’s security.
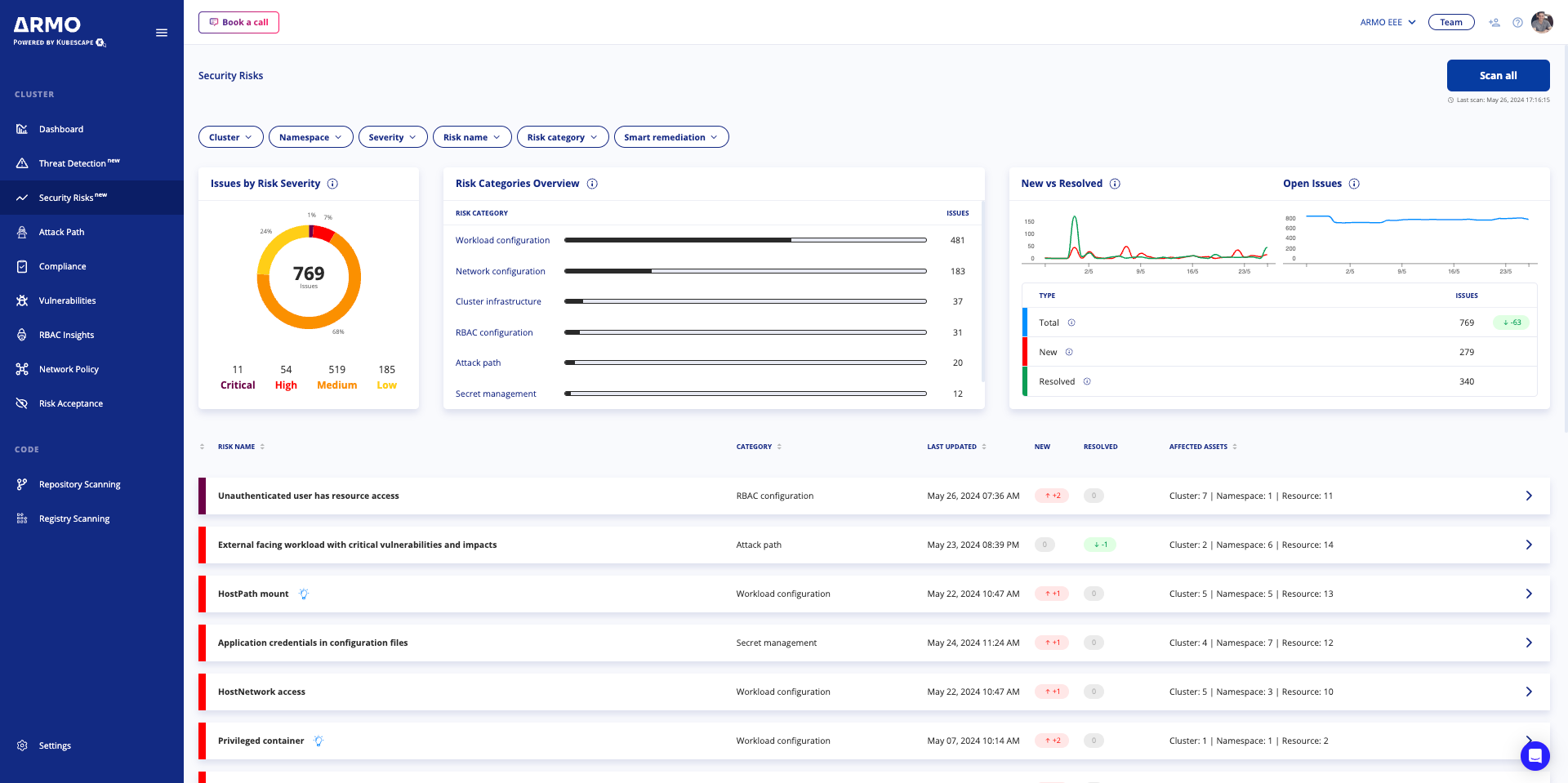
Security Risks provides an overview of potential vulnerabilities in your cluster environment such as configuration risks, workload risks, network risks, and compliance risks. It details potential vulnerabilities like misconfigurations, insecure workloads, network exposures, and non-compliance issues, and provides best practices for mitigating these risks. For more detailed information, please navigate to Security Risk
Next steps
Now that you’ve explored a little of what ARMO Platform can offer, check out these topics to see what else we can do.
Updated 3 months ago


