Onboard AWS Organization
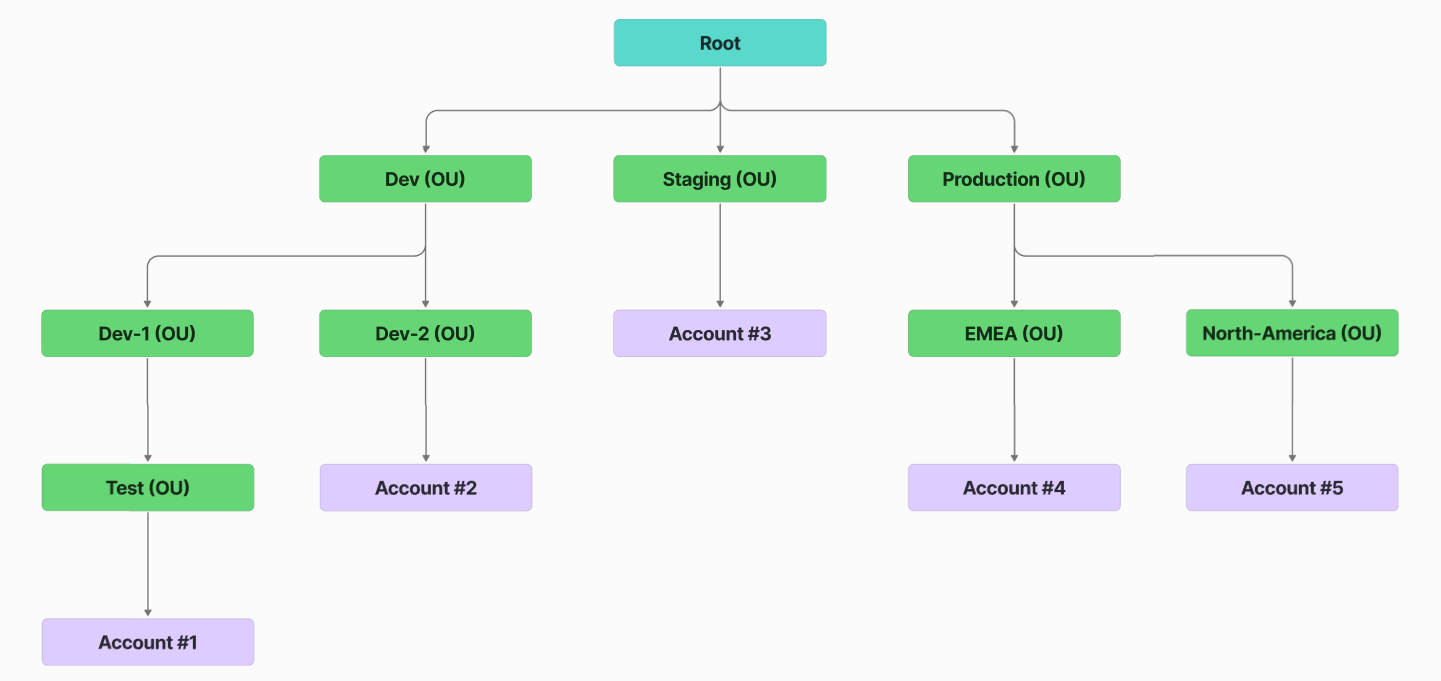
Organizations that manage their AWS services and resources through AWS Organizations can onboard their management (root) account to ARMO. Once AWS Organizations is enabled in the AWS Management Console and the management (payer) account is connected, ARMO automatically discovers and onboards all member accounts within the organization in a single, streamlined process.
Overview & Objectives
Purpose:
This document describes how to onboard an AWS Organization (i.e. the master account plus member accounts) into ARMO Platform. The goal is to enable unified visibility, governance, and security controls across all AWS accounts under that Organization.
Prerequisites
| Item | Requirement |
|---|---|
| ARMO | You have an admin or Manager access to ARMO Platform |
| AWS Organization | You have an AWS Organization with a master (management) account or delegated admin accounts and member accounts. |
| IAM permissions | You (or roles you’ll use) can create IAM roles, attach policies, and grant cross-account role assumption permissions. |
High-Level Onboarding Flow
Here’s the sequence of steps at a high level:
- In ARMO Platform: initiate the connect Amazon Web Services Organization flow.
- In the AWS management (root / payer) account: create an IAM role (the “ARMO Organization Role”) with a trust policy and attach the required permissions.
- Configure that role as the organization-level connection in ARMO.
- ARMO will detect all member accounts and propagate read only roles into them.
- ARMO can access all accounts and resources for scanning purpose
- The data is being ingested correctly and present in the ARMO platform.
Detailed Step-by-Step Onboarding
Step 1: Start in ARMO
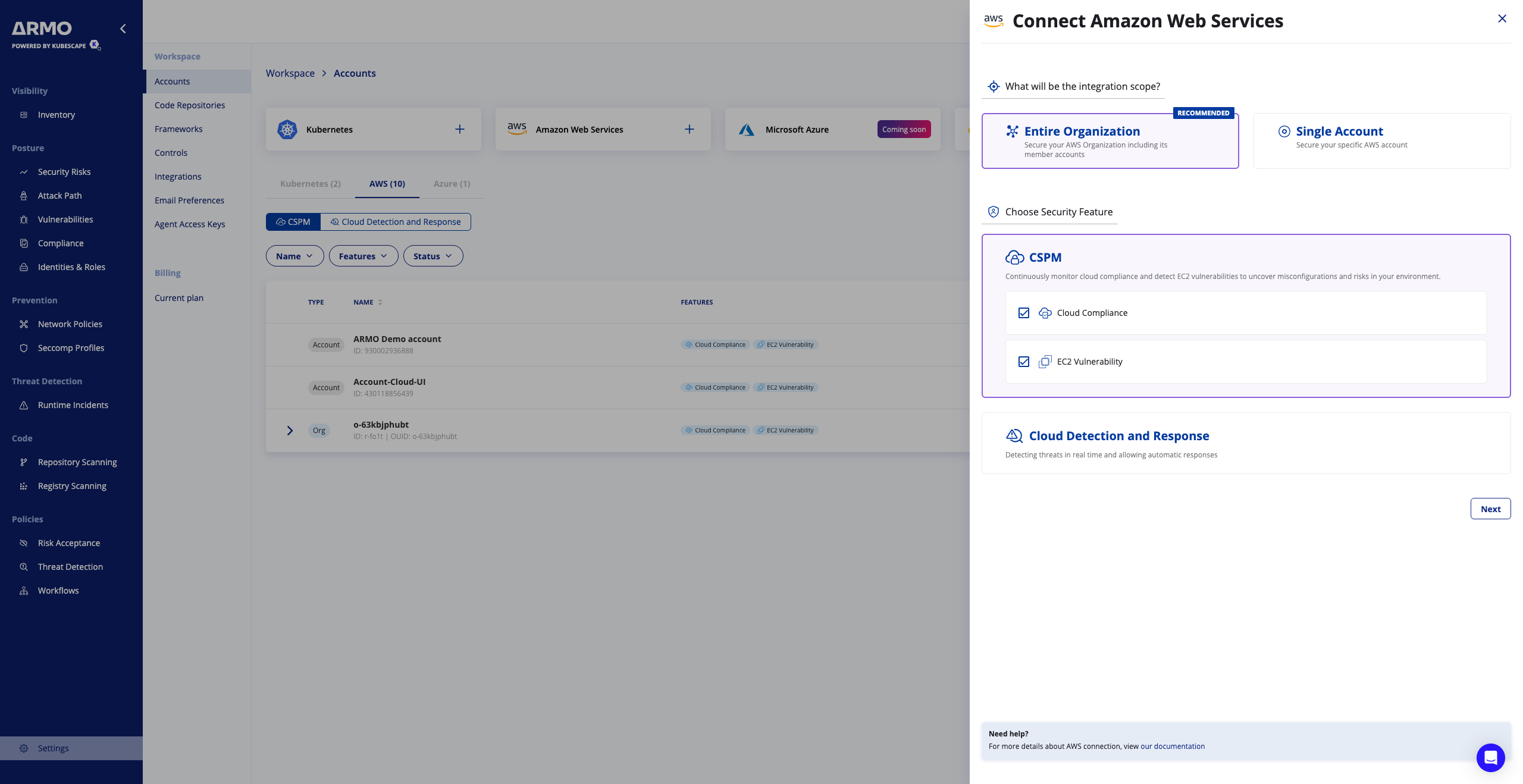
- Log in to the ARMO Platform and navigate to Settings → Accounts → AWS
- Click the Amazon Web Services card select Entire Organization as the type of cloud account to onboard.
- Choose the Security features (Compliance, Vulnerabilities ) and click next
- Choose an AWS Region to launch your stack, and click Launch Stack
Step 2: Create IAM Role in AWS Management Account
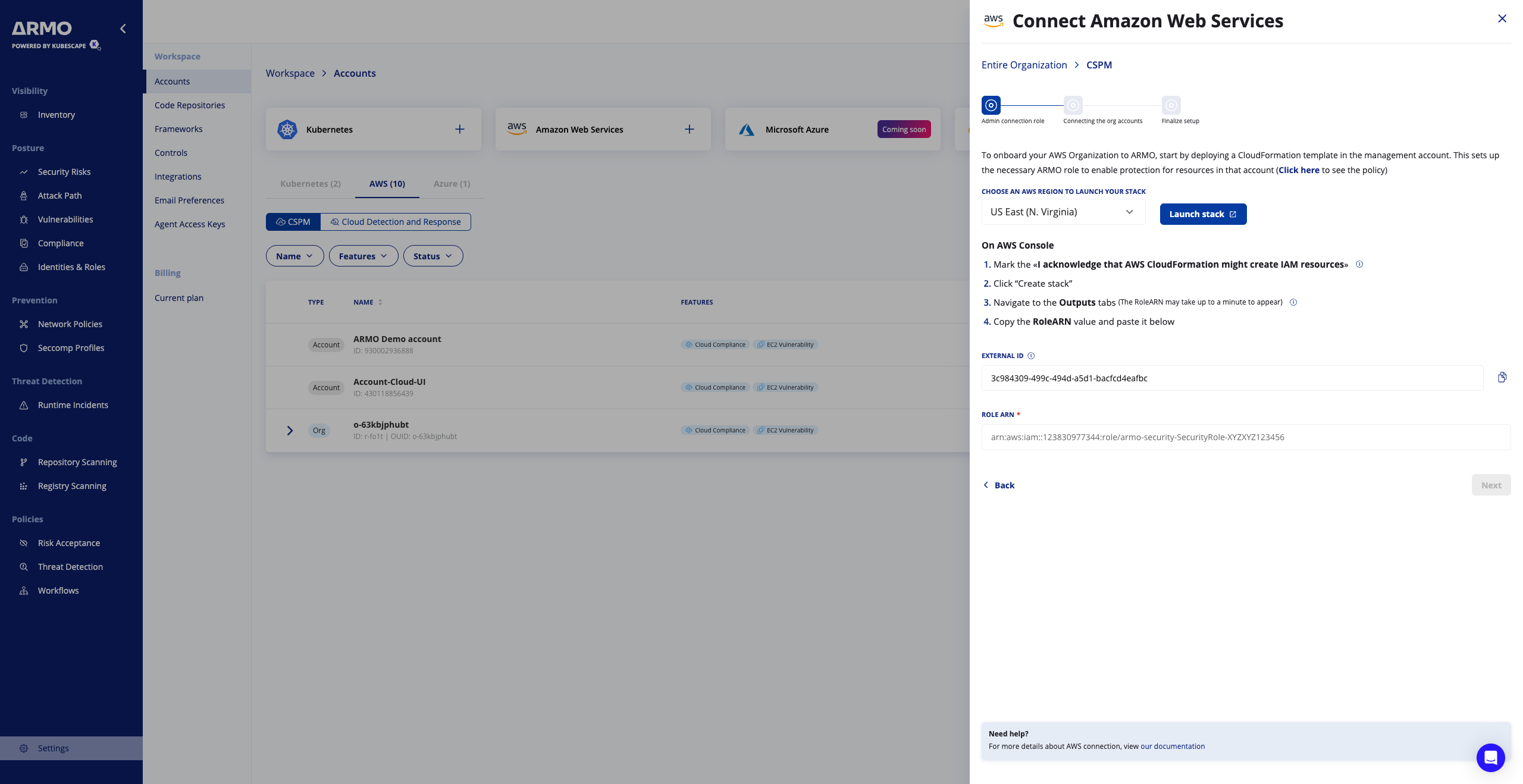
The AWS console will present you with a CloudFormation template, IAM trust policy, and instructions to deploy in AWS management account:
-
Provide a stack name, e.g. armo-org-discovery-stack

-
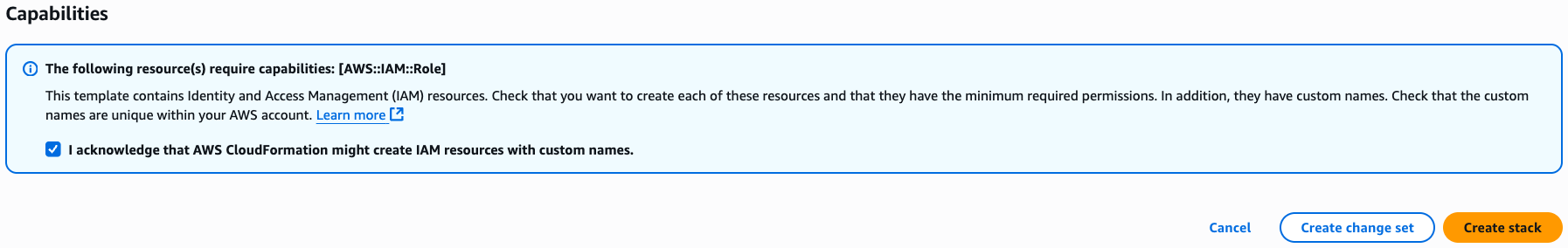
Scroll to the bottom and Mark the «I acknowledge that AWS CloudFormation might create IAM resources with custom names»
-
Click “Create stack”
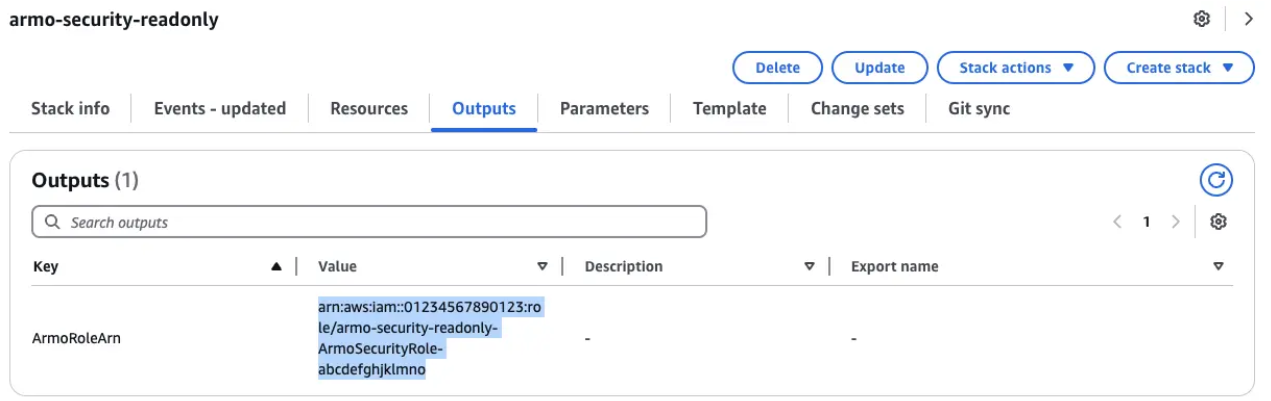
-
Navigate to the Outputs tabs (The RoleARN may take up to a minute to appear)
-
Copy the RoleARN value
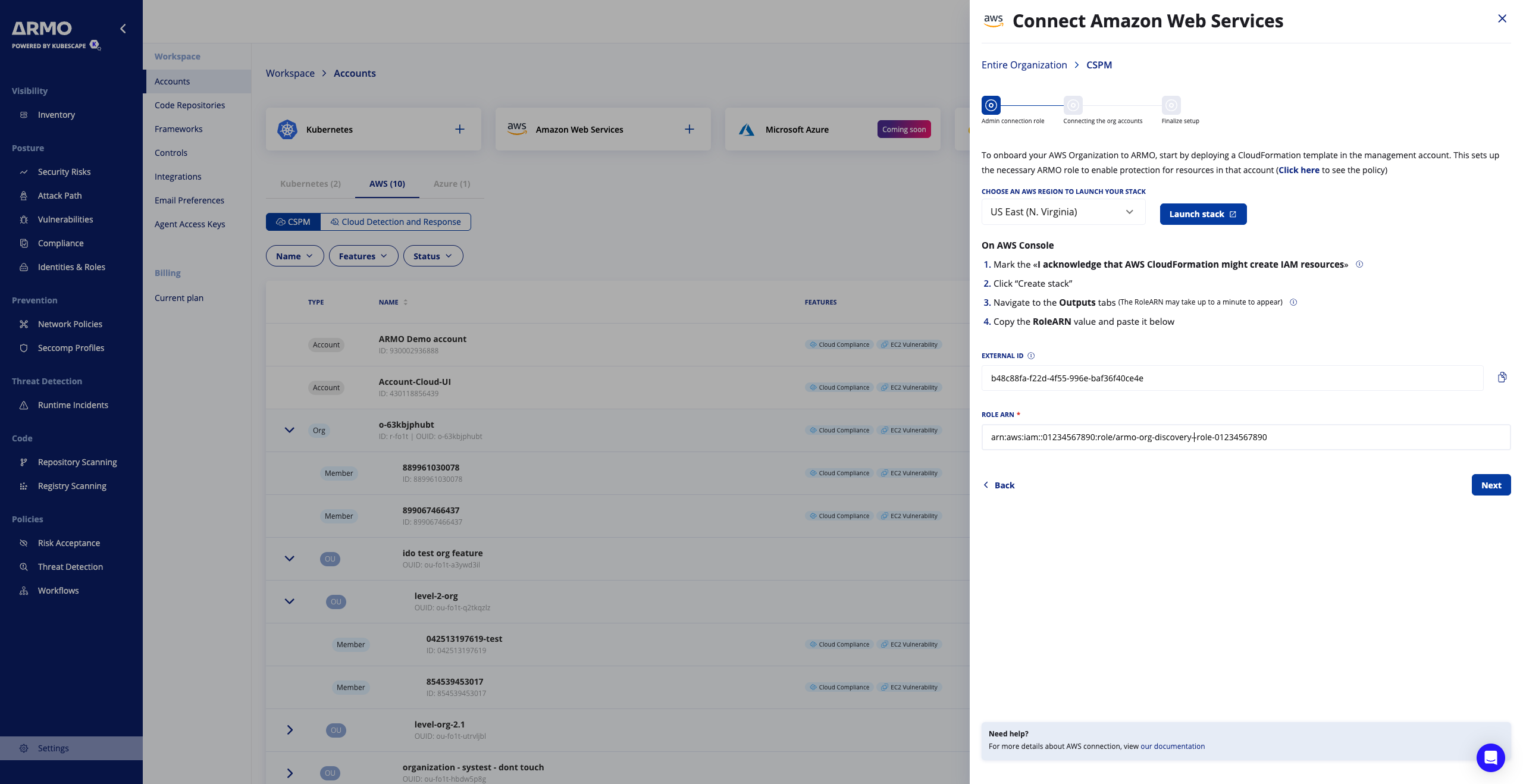
Step 3: Configure the Role in ARMO Platform
-
Back in ARMO, paste the Role ARN of the role you just created (e.g. arn:aws:iam::<management_account_id>:role/armo-org-discovery-role).
-
Click Next
-
ARMO will attempt to assume that role in the management account and list all AWS accounts in the Organization.
Step 4: Onboard Member Accounts
ARMO uses AWS CloudFormation StackSets to connect to your AWS Organization by deploying a read-only IAM role across all accounts in one operation
-
Back in ARMO, Click on ״Launch StackSet״ to continue and follow the steps on the ARMO connection wizard
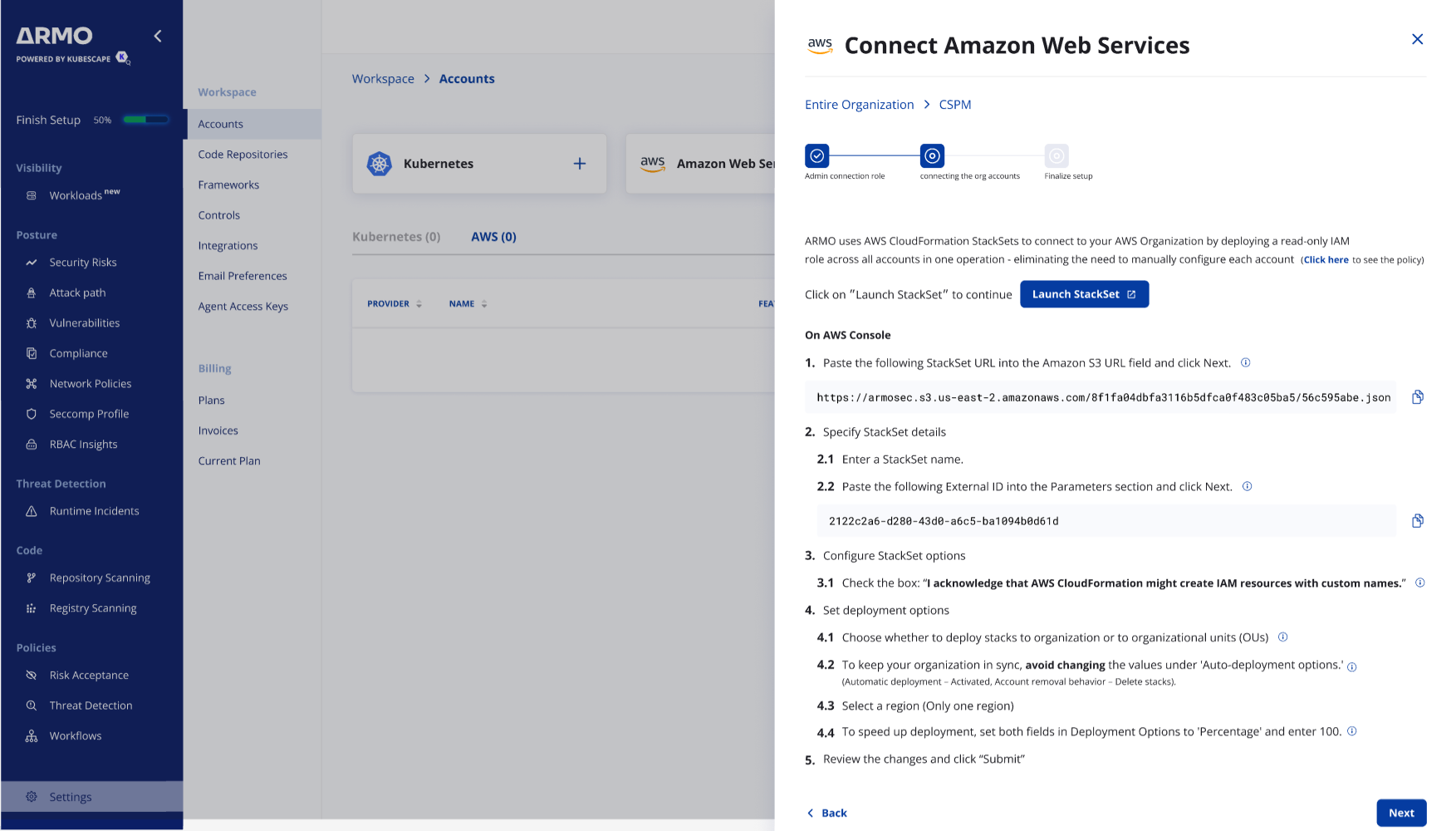
-
The AWS console will present you with a Create StackSet wizard that for each member account, deploy a delegated IAM role (e.g. ArmoSecurityCloudMemberRole) with the required read only permissions
-
Back in ARMO, Click Next
-
Enter a Display name for the organization
-
(Optional) enter account ids you would like to exclude
-
Click Connect organization
Step 5: Confirm Data Ingestion & Monitoring
- In ARMO, verify that all accounts under the AWS Organization appear in the Settings / Accounts / AWS table.
- Check that ARMO is showing the scanning results on the Compliance > Cloud or Vulnerabilities > Host pages (depending to the feature selection)
- Validate data freshness (e.g. that ARMO is syncing on its schedule).
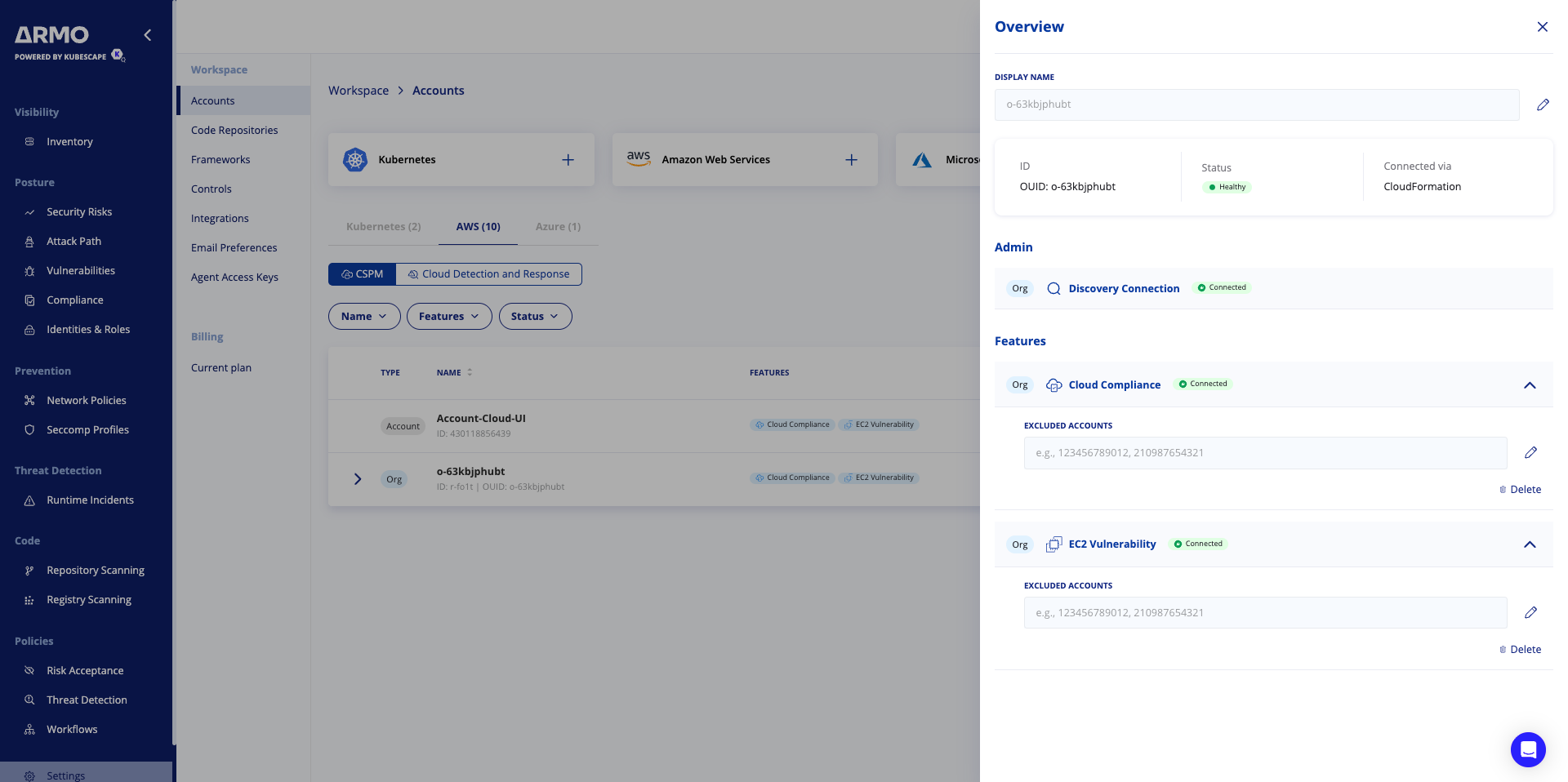
Exclude Accounts (Optional)
This configuration allows you to exclude specific accounts from the selected OUIDs
Exclude Accounts
- Prevent specific accounts from being onboarded under the selected OUIDs.
- These accounts will be excluded from scanning and monitoring.
Troubleshooting
| Issue | Likely Cause | Suggested Fix |
|---|---|---|
| ARMO shows “unable to assume role” | Trust relationship or External ID mismatch | Verify the Role ARN, trust policy, and external ID used in ARMO |
| Some member accounts don’t appear | Permissions lacking in organization role or missing stack deployment | Ensure the organization role has rights to list accounts and deploy stack sets; check CloudFormation deployment logs |
| Missing resources type | 1. The IAM policy is too restrictive 2. SCP | Add missing Read / List permissions for APIs ARMO needs |
Updated 3 months ago
